This article describes how to configure LDAP for Cisco ASA AnyConnect Secure Mobility VPN
- In your OneLogin environment, navigate to Administration > Authentication > VLDAP. Click New Configuration, then configure a new VLDAP config.
Sample config:
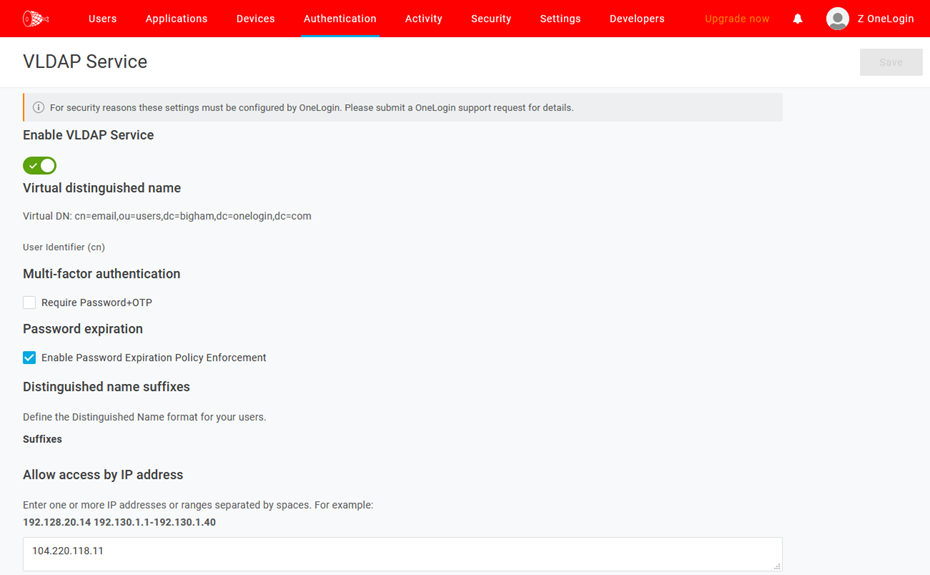 Username or sAMAccountName are also supported via alternate configurations on both the OneLogin VLDAP and the Cisco ASA. You must first request OneLogin support to configure your VLDAP configuration to use sAMAccountName or username as your cn value instead of email.
Username or sAMAccountName are also supported via alternate configurations on both the OneLogin VLDAP and the Cisco ASA. You must first request OneLogin support to configure your VLDAP configuration to use sAMAccountName or username as your cn value instead of email. - Navigate to Users > Users and create a OneLogin user to act as your VLDAP service account. Apply a privilege of Manage users, Manage group, or Super user to your VLDAP service account.
Sample user with privileges assigned:
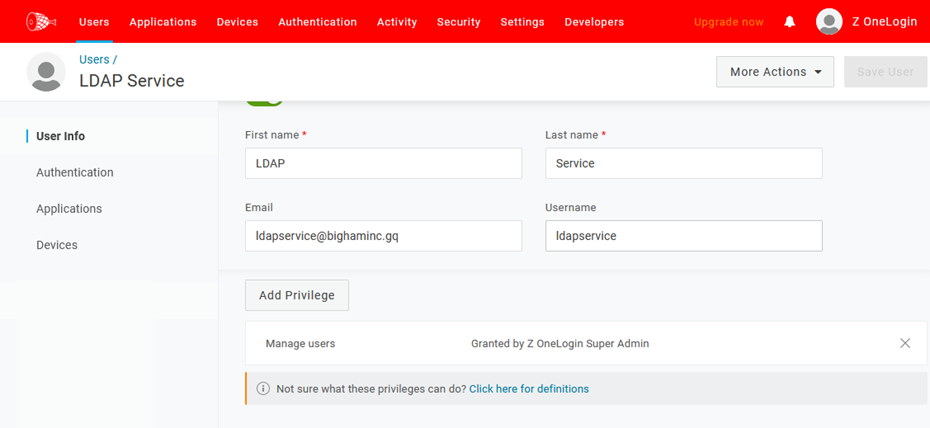
-
Note: This step applies to Cisco ASA software version 9.13(1) or later, due to Cisco ‘certificate validation’ requirements introduced at that time of that release.Download the DigiCert SHA2 Secure Server CA certificate to your local workstation. Login to your Cisco ASA device via ASDM with your administrative account, and navigate to Configuration > Certificate Management > CA Certificates. Click Add, enter a Trustpoint Name (e.g. DigiCert_SHA2_Secure_Server_CA), and click Install Certificate
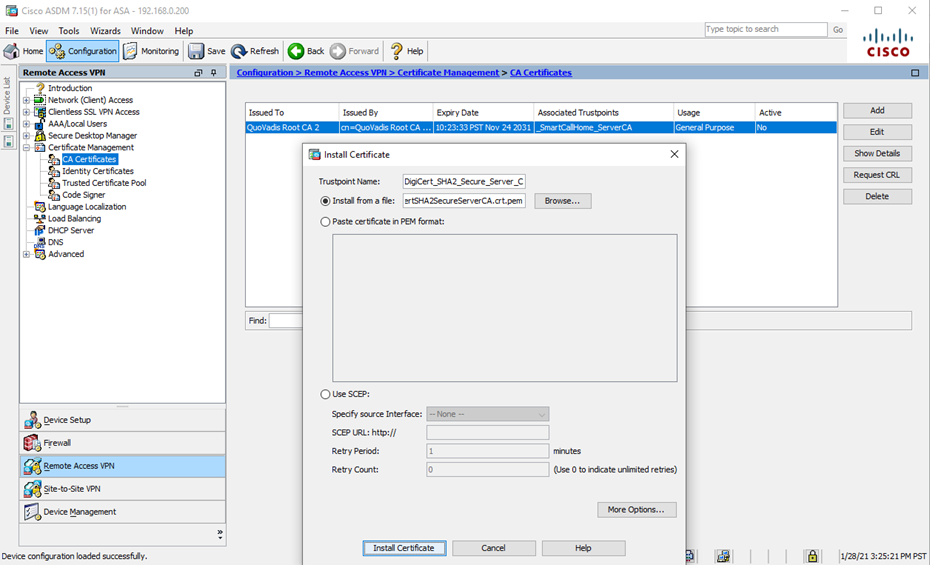
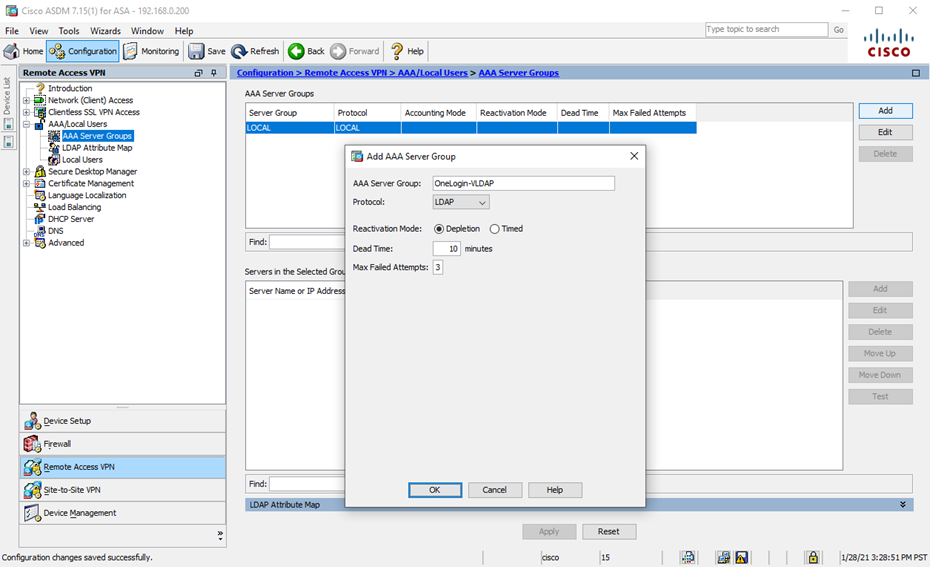
- Navigate to Configuration > Remote Access VPN > AAA/Local Users > AAA Server Groups and click Add in the upper-right. Enter an AAA Server Group name of your choosing, confirm the Protocol is set as LDAP, and then click OK.
- Select your newly created AAA Server Group in the upper menu and then click the lower-right Add (next to the lower menu). Configure the AAA Server by using your region-specific settings as outlined in OneLogin Virtual LDAP Service.
(If you don't know whether your OneLogin account is in the US or EU region, please contact OneLogin support.)
Interface Name: outside Server Name or IP Address: ldap.us.onelogin.com Timeout: 30 Seconds Enable LDAP over SSL: Checked/Enabled Server Port: 636 Server Type: -- Detect Automatically/Use Generic Type -- Base DN: ou=users,dc=bigham,dc=onelogin,dc=com Scope: All levels beneath the Base DN Naming Attribute: cn Login DN: CN=ldapservice@bighaminc.gq,ou=users,dc=bigham,dc=onelogin,dc=com Login Password: password for your Login DN account 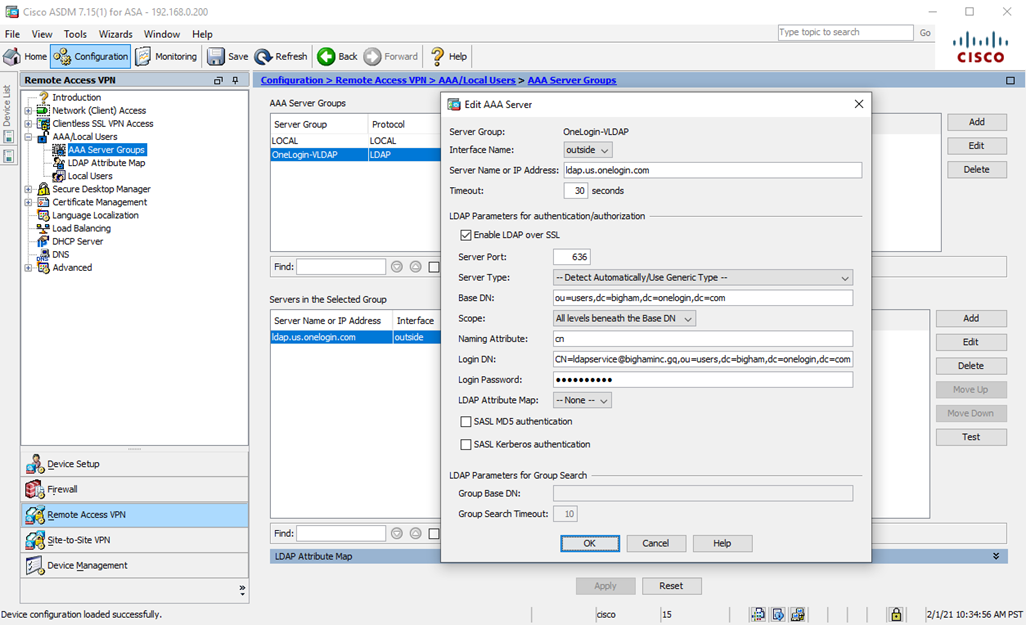 When possible, use the VLDAP server domain name rather than the IP address, as IP addresses may change.
When possible, use the VLDAP server domain name rather than the IP address, as IP addresses may change. - Click Apply to save your new configuration.
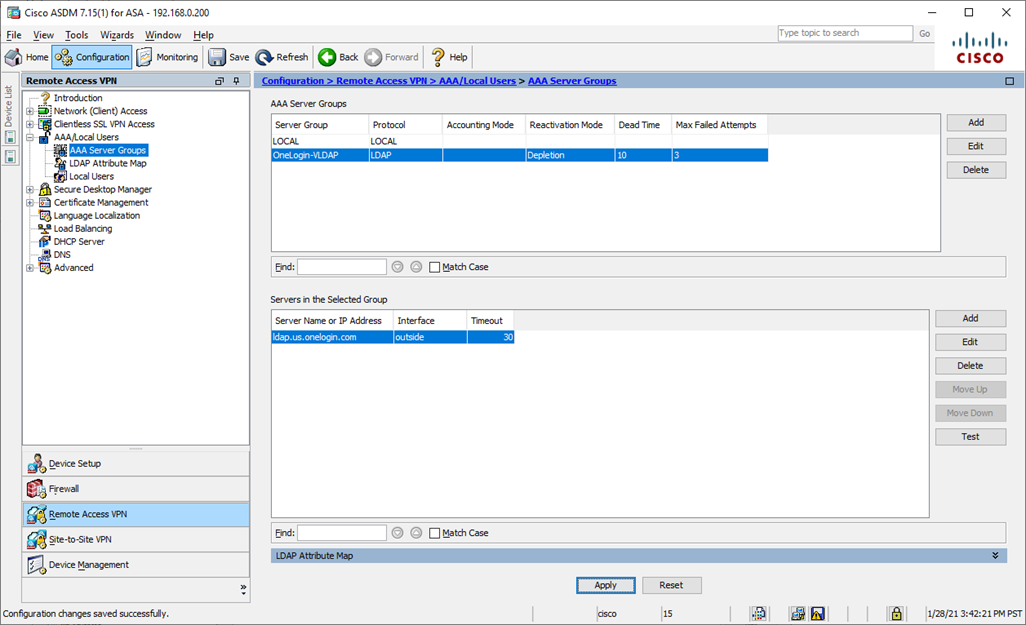
- Test your new AAA Server Group by selecting AAA Server Group on the top menu, highlighting the AAA Server in the bottom menu, and then clicking Test.
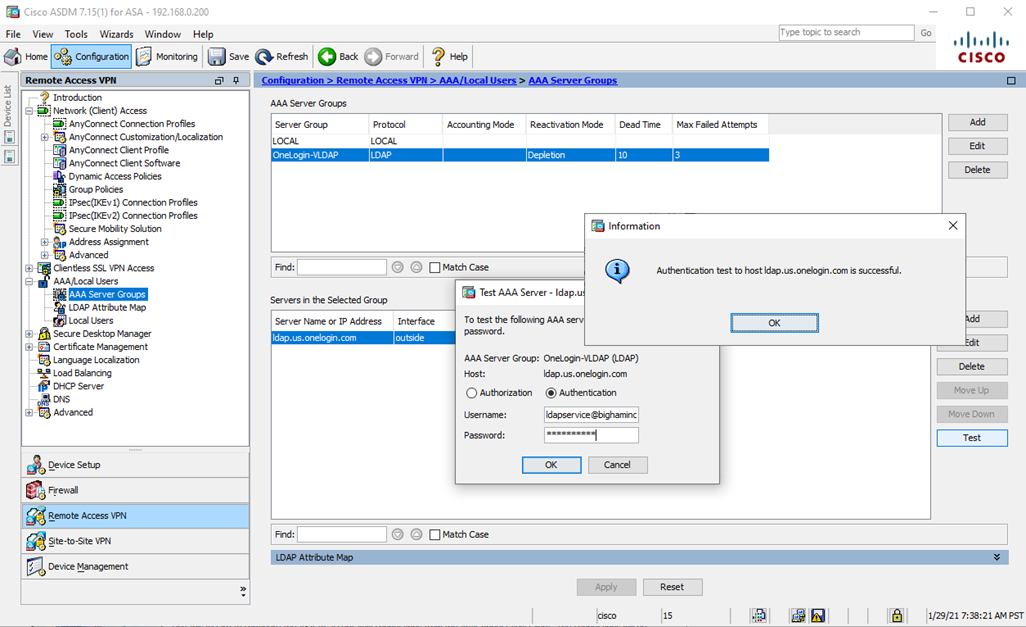 If your test fails with the following error message, first validate that all of the settings outlined in Step 5 are correct. Then confirm that your VLDAP service account is not locked out within OneLogin and has a valid password without an MFA requirement.
If your test fails with the following error message, first validate that all of the settings outlined in Step 5 are correct. Then confirm that your VLDAP service account is not locked out within OneLogin and has a valid password without an MFA requirement.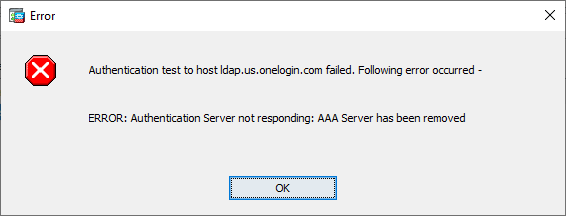
- To set up a new AnyConnect VPN configuration for testing purposes, navigate to Wizards > VPN Wizards > AnyConnect VPN Wizard and click Next at the initial screen.
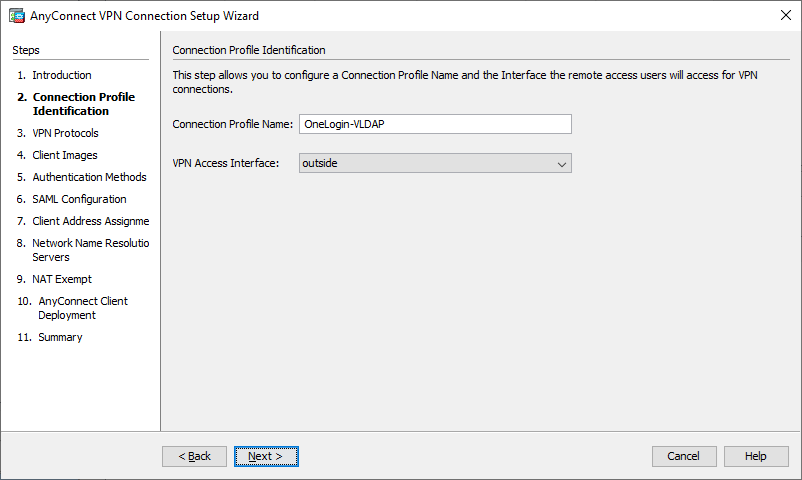
- Enter a Connection Profile Name of your choice and click the Next button.
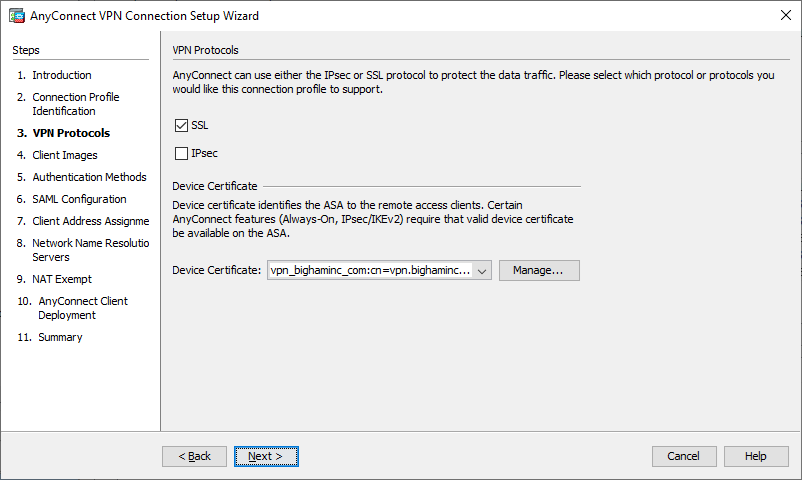
- Confirm SSL is checked and IPsec is unchecked. Choose your relevant Certificate Authority Device Certificate, and then click Next.
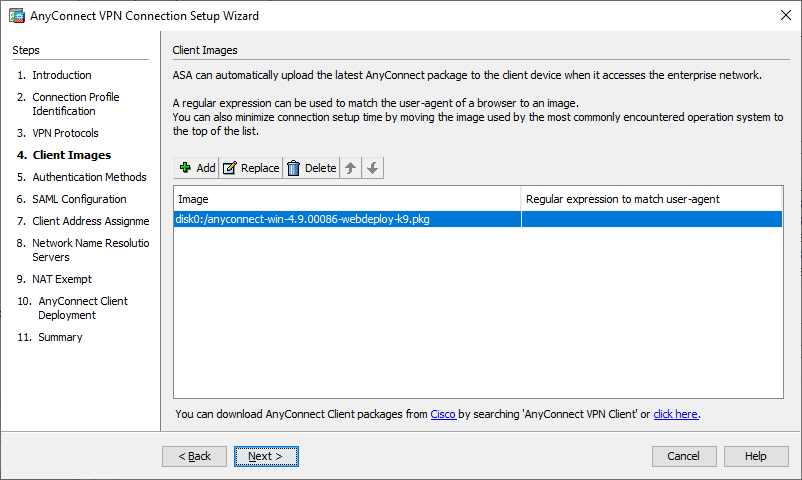
- Choose your relevant Client Image(s) and click Next.
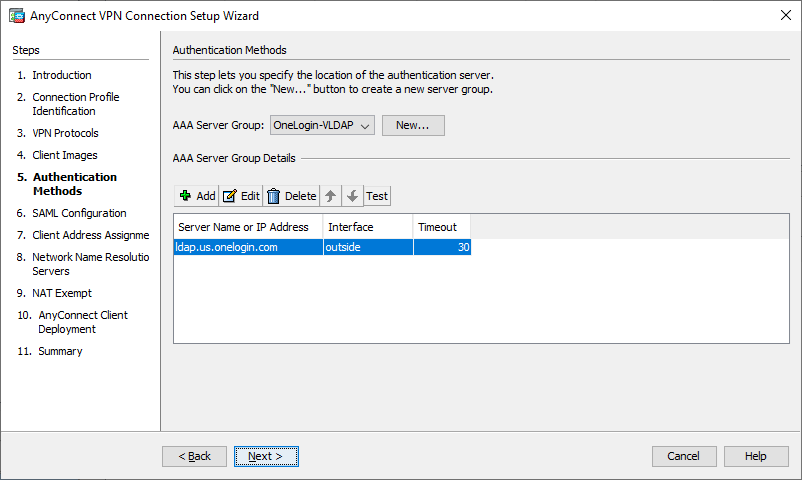
- Choose the AAA Server Group that you previously created and click the Next button.
- Click Next to skip the SAML Configuration option.
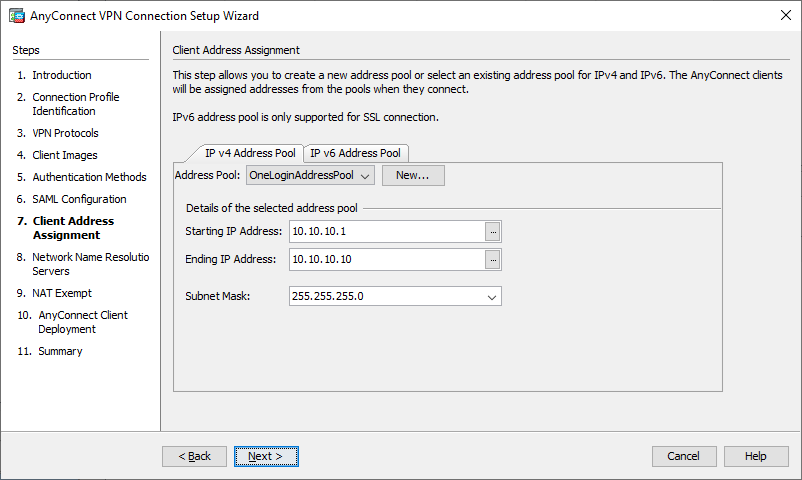
- Select your relevant Address Pool and then click the Next button.
- Confirm your DNS settings and then click Next.
- Select/Deselect the NAT Exempt option to align with your VPN needs and click Next.
- On the following screen, click Next.
- Review/Validate your settings and then click Finish.
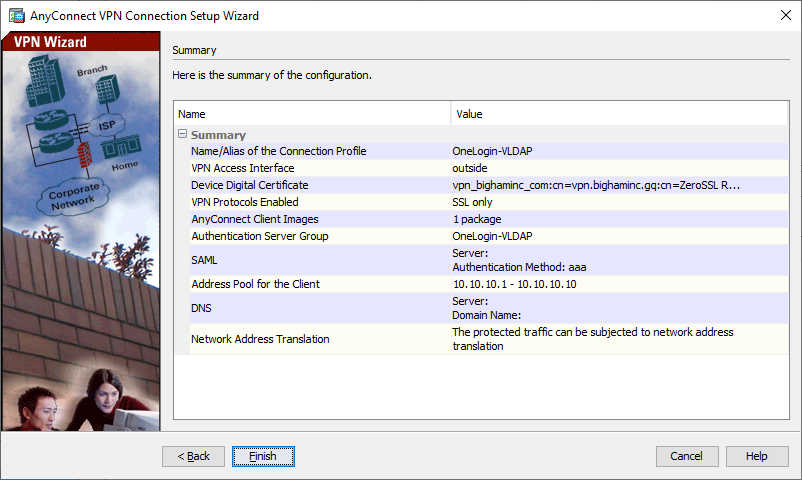
- Navigate to Configuration > Remote Access VPN > Clientless SSL VPN Access > Connection Profiles, select your newly created Connection Profile, and click Edit to review your Connection Profile.

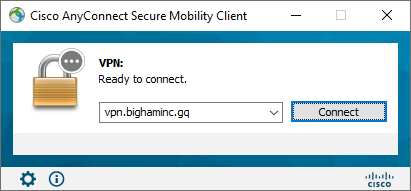
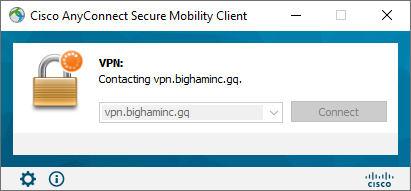
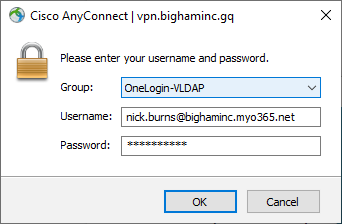
- Test via your Cisco AnyConnect Secure Mobility client:
Troubleshooting
Issue: Employees receive a ‘Login Failed’ error message via Anyconenct despite entering their correct password.
Solution: The employee is trying to login with username or sAMAccountName but your OneLogin VLDAP configuration is set up to require the default DN of email. Instruct the employee to use their email address or reconfigure your Cisco ASA and OneLogin VLDAP to use either username or sAMAccountName as the DN.