|
User policies provide you and your organization with the best security requirements for your needs, by allowing you to choose specific security restrictions and protocols, then apply them to either individual users or to Groups. This article goes over how to configure and manage user policies.
User Policy Management
The Default User Policy
Each OneLogin tenant comes configured with a default user policy that's automatically applied to all user accounts until they're assigned a different policy.
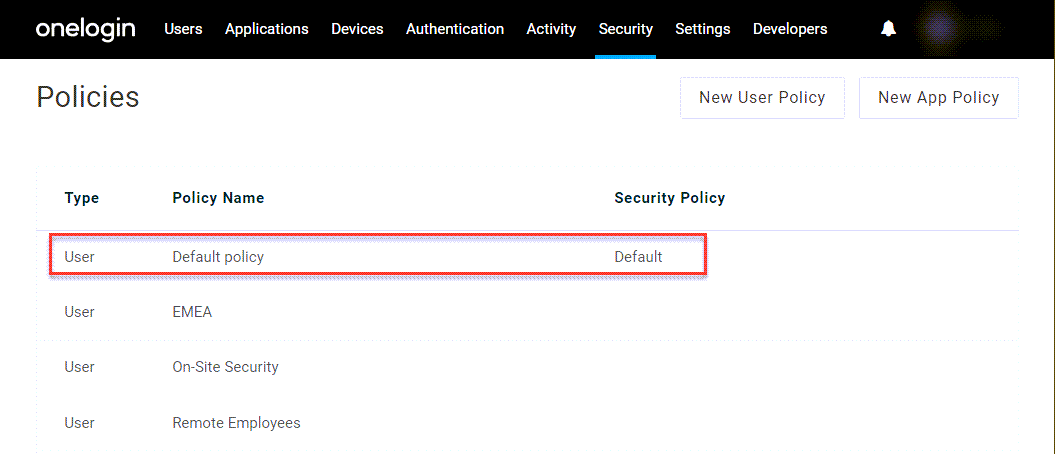
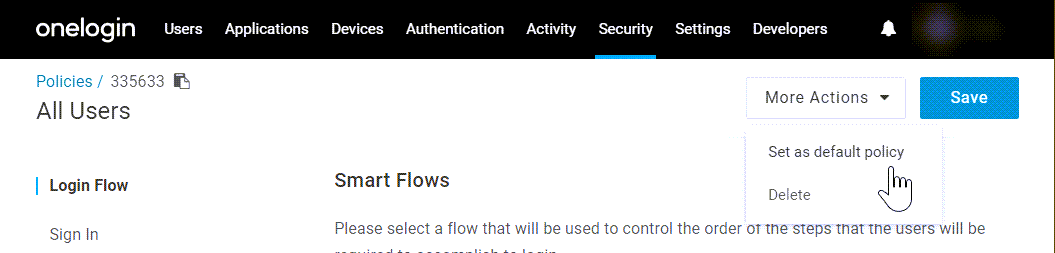
If you want to change your default policy, you can edit the existing default, or you can create a new user policy and make it the default by opening its More Actions menu and selecting Set as default policy.
Creating User Policies
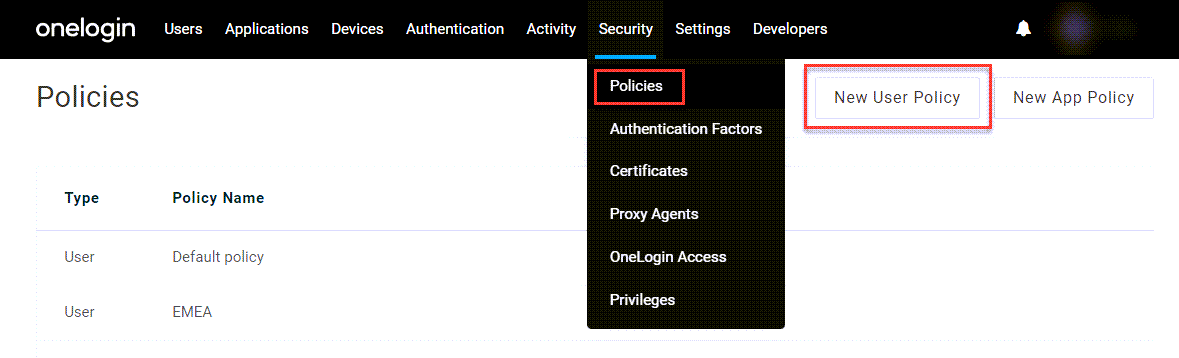
To create a new user policy, go to Security > Policies in your OneLogin admin portal and click New User Policy.
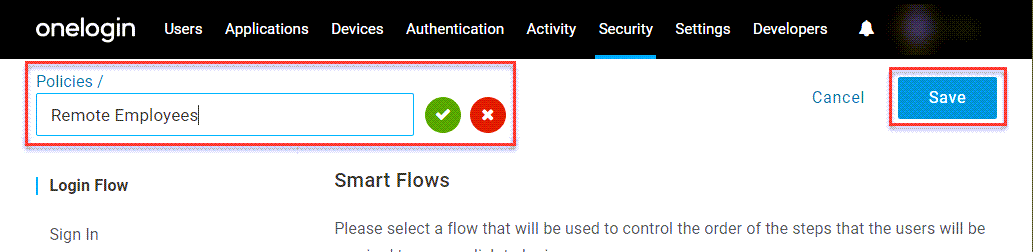
Give the policy a descriptive name, such as its purpose or the group it will be applied to, and click Save.
Deleting User Policies
To remove an unneeded user policy, open its More Actions menu and select Delete. All users currently assigned to that policy will be reverted to the default user policy.
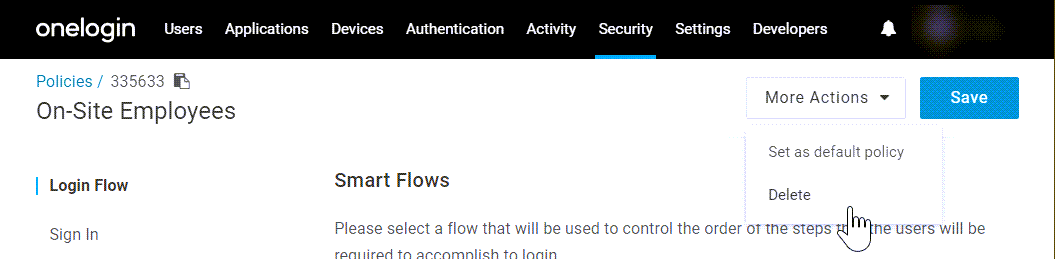
Note: The default user policy cannot be deleted. If you wish to remove your default policy, another policy must first be set as the new default.
Assigning User Policies
User policies are best assigned via groups, which will apply the policy you select to all users added to that group.

If necessary, you can also manually assign a policy to an individual user by editing the user, going to Authentication, and selecting your desired policy from the User security policy menu.
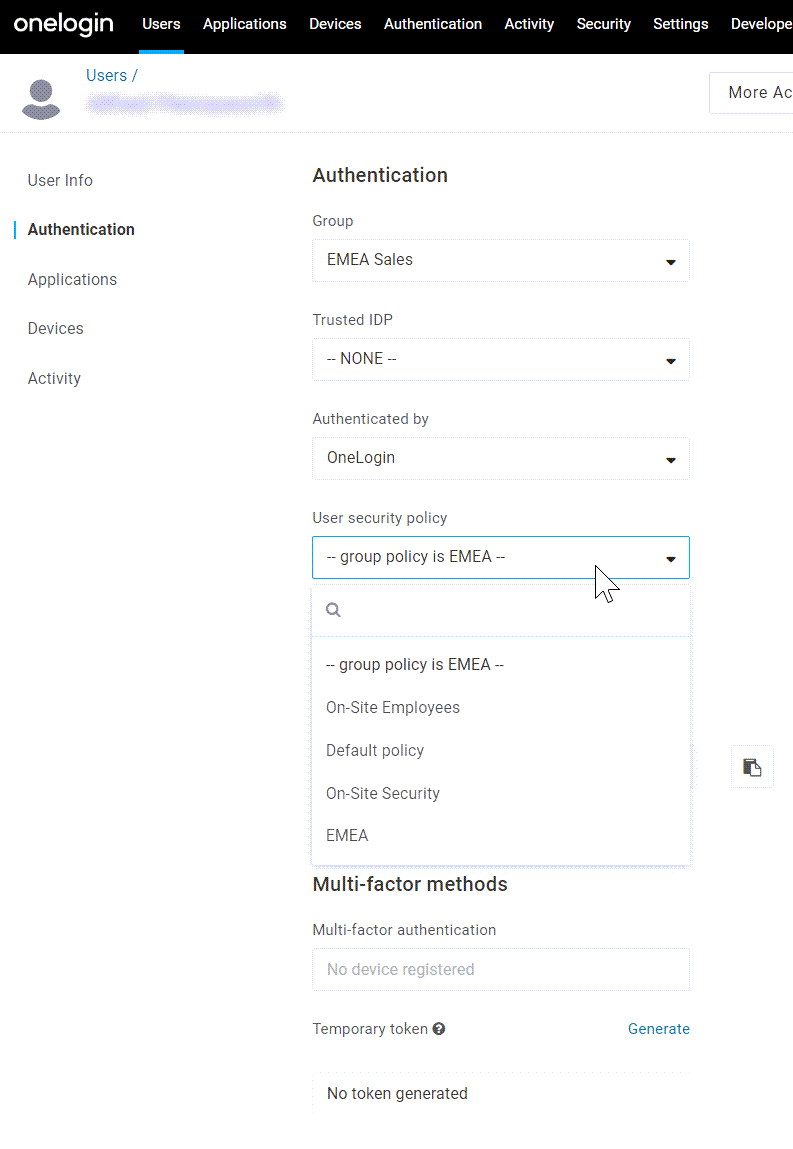
Note: Manually assigned user policies will always override group policy assignments, even if the user is later added to a different group. To revert a user back to automatic policy assignments, you must return to their user settings and assign them the first policy option.
User Policy Configuration
Login Flow
Smart Flows
Smart Flows allow you to define and customize specific login flows on a user policy, based on your organization's security and end-user requirements.
|
Standard
|
ID/Password/MFA
|
This is the typical authentication flow deployed by most organizations. Select it if you're not sure which flow to use.
|
|
Brute-Force Defense
|
ID/MFA/Password
|
This flow helps to prevent account lockouts if your organization authenticates against Active Directory. Select it to protect against attempts at accessing your org's resources by exhausting all possible password combinations.
|
|
Passwordless
|
ID/MFA
|
This passwordless authentication flow is a user friendly approach that requires only a username and an auth factor. Select it if you use Webauthn or OneLogin Protect.
|
At this time, it is not possible for user policies to dynamically change flows. You must choose a single flow to apply to all users within any given policy.
Sign In
Terms and Conditions
If Require users to agree to Terms and Conditions is enabled, a text area appears where you can enter your Terms and Conditions with markdown formatting. All future users will be required to accept these conditions the first time that they sign in.
This is similar to the System Use Notification option, but while the system use notification will appear every time a user accesses OneLogin, the Terms and Conditions are displayed only during a user's first login.
Social Sign-In
If Enable is checked, the major social networks appear as additional options. Be sure that you have configured a trusted IdP (TIdP) for any social network you wish to allow your users to authenticate with, then check its corresponding box to allow it for your any users with this policy assigned.
Note: If you enable this feature, multi-factor authentication (MFA) will be disabled for users using these social credentials. If you later decide to disable one of the social networks, all users authenticating with that provider will be unable to sign in until they have created a new OneLogin password.
OneLogin Desktop
|
Apply MFA policy requirement when logging into laptop and desktop devices
|
Enable this setting to prompt users to authenticate with MFA when signing in using OneLogin Desktop.
This setting is only available with OneLogin Desktop for Windows.
|
|
Don't require browser login for trusted devices
|
Enable this setting to use the OneLogin Desktop certificate as a primary authentication factor and, allowing users to enjoy passwordless entry into the portal.
Note: Depending on your MFA settings, users may still be prompted for other authentication factors.
|
Browser Extension
|
Allow users to install browser extensions from their Profile page
|
Enable this setting to provide users with a download link to manually install the OneLogin browser extension from their user portal. OneLogin will still automatically prompt users without the extension to install it when they attempt to access an app that requires it.
|
Portal App Store
|
Users can browse and add Company apps from the App Store
|
Enable this setting to allow the OneLogin browser extension to prompt users to save their login data for recognized company applications the first time they sign in.
|
|
Users can browse and add Personal apps from the App Store
|
Enable this setting to allow the OneLogin browser extension to prompt users to save their login data for other applications the first time they sign in.
|
Security Questions
Enable this setting to require users to configure answers to their security questions in their OneLogin profile. This setting will be unavailable unless you have both configured OneLogin Security Questions as an authentication factor, and enabled them in the MFA section of this user policy. If you have them configured and enabled but do not enable this setting, security questions will be available but optional in your users' profile settings.
Auto suspend inactive users
Enable this setting to automatically suspend users who haven't signed in to OneLogin for 90 days, including users that received an invitation to join but never logged in. When a user is suspended, an event is logged detailing the suspension.
User Invitation Link Timeout
Specify the timeout value of invitation links. The default value is 24 hours.
NOTE: One Identity recommends setting the timeout value to 72 hours or less.
Password
Password Settings
Age and History
|
Maximum Password Age
|
Enter the amount of time in days that a user's password remains valid before it must be changed. Enter 0 to disable this requirement. If you use a third-party directory that doesn't allow password expiration with OneLogin, your directory will respect OneLogin's policy-based password expiration settings.
|
|
Enforce Password History
|
Enter the number of unique new passwords that must be associated with a user account before an old password can be reused. For example, if 5 is entered, users cannot reuse any of their last five passwords. Enter 0 to disable this requirement.
|
|
Minimum password length
|
Enter the minimum number of characters required for new passwords.
|
Password Complexity
Choose the combination of different character types required for new OneLogin passwords. If a user is authenticated by an external directory, the directory settings determine which policy applies.
Note: Changing password complexity requirements will not force users to change existing passwords that do not currently meet the new requirements. Requirements will apply only to passwords newly created or changed after saving this policy. If necessary, you may use a bulk operation for force password reset for existing users.
Password Restrictions
|
User attributes not allowed in password
|
Select any user attributes you want to prevent users from including in their passwords, such as their username or phone number.
|
|
Enforce account password block list
|
Enable this setting to prevent users with this policy from creating passwords that include any of the keywords block-listed in your account settings.
|
Compromised credentials
When a user creates a new account or changes their account password, the Compromised Credential Check compares their new username and password against a dynamic and continuously updated database of credentials that have been breached and posted on the dark web and prevents them from using any credentials identified as compromised. Enforce compromised password check offers the most comprehensive coverage, preventing any compromised password from being used.
|
Enforce compromised credential check
|
Select this option to check the user's full credentials and verify that their unique combination of username and password is not included in the known compromised credentials.
Enforce compromised credential check only blocks the combination of username and password that have been compromised; if you want to block your users from using any compromised password, choose Enforce compromised password check instead.
|
|
Enforce compromised password check
|
Select this option to check only the user's password against the compromised credentials, regardless of username.
|
|
Don't perform the check
|
Select this option to disable Compromised Credential Check.
|
Important: Compromised Credential Check is only applied when new credentials are added or changed. It does not audit existing credentials that were created prior to enabling the setting.
Password Reset Redirect
If you maintain user passwords in a third-party directory, you can redirect your users to an external password reset site when they attempt to change their password using OneLogin. Enable this setting to enter an external URL where users will be directed when they initiate a password reset, as well as a markdown-formatted message for your users. If the text field is left blank, users will be prompted to continue with the default text: "You will now be redirected to reset your password."
If this setting is left disabled, or if the URL field is left blank, users will be directed to the default OneLogin password reset URL when they initiate a password reset: https://your-domain.onelogin.com/login2#action=password_reset
Note: You don't need to use password reset redirects if all of your OneLogin users are managed in the same third-party user directory. This feature is best used with a multi-directory environment that contains different users in each directory.
Account Recovery
Password Update
|
Allow users to update their directory password
|
Enable this setting to provide a Forgot Password link on the login page where users can reset their own passwords after verifying their identity with an authentication factor. You can decide which verification options to offer under Select Factors Available, such as Email or any other authentication factors that you have previously configured.
This setting also determines whether new users receive a password creation link in their initial invitation to use OneLogin.
|
|
Allow users to unlock their accounts
|
Enable this setting to allow users to unlock their own accounts in the event that they're locked out after too many incorrect login attempts. The user is directed to https://your-subdomainonelogin.com/login2#action=unlock_account to verify their identity with one of the authentication factors selected under Select Factors Available, then given the choice to only unlock their account or to both unlock the account and reset their password.
Speak to your account manager to activate this setting. This setting cannot be combined with email authentication. If the setting is unavailable, confirm that it has been activated by your account manager and that Email is unchecked under Select Factors Available.
|
|
Require reCAPTCHA
|
Enable this setting to require users to complete a reCAPTCHA prompt before they can update their passwords or unlock their accounts, helping to prevent automated bot attacks.
|
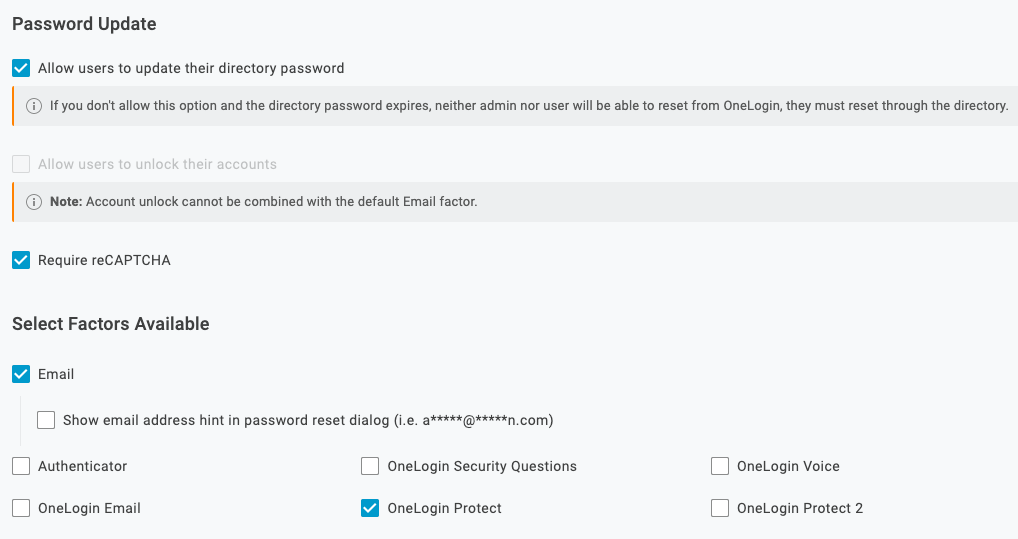
Disable OneLogin Protect Account Recovery Notifications
|
Disable Account Recovery Notifications
|
When checked, OneLogin Protect push notifications will be disabled for account recovery. You can also choose to disable login push notifications in MFA.
|
Secure OneLogin Areas
Securing specific OneLogin areas allows you to protect your users and administrators from being locked out of their accounts or having specific account actions hijacked by bad actors. With secured areas enabled, additional security policies will be applied before a user can access certain areas like the user profile settings or admin portal. For example, a user might be prompted to verify additional authentication factors before changing their password.
-
Secure Administration Portal applies your selected app policy before allowing administrators to access the admin portal.
-
Secure User Profile applies your selected app policy before allowing users to access certain settings in their user profile, such as changing their password or adding or removing authentication factors.
- OTP session timeout allows you to specify the session timeout value. The maximum value is 60 minutes.
Session
Login attempts
|
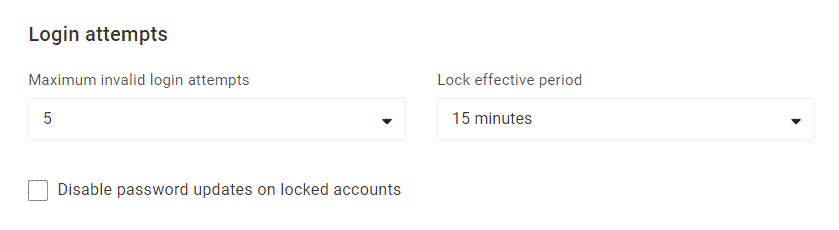
Maximum invalid login attempts
|
Select the number of consecutive times that the wrong password can be entered before locking an account. If the user successfully signs in or resets their password before the account is locked, then the count is reset to 0. You can choose any number 3-10, or No limit to disable account locks.
|
|
Lock effective period
|
Select the amount of time that the account remains locked before the user can attempt to log in again. You can choose from 15, 30, or 60 minutes, or Until Unlocked to prevent locked accounts from automatically allowing any future attempts.
Note: Although the user may attempt to sign in again after the lock effective period is up, the account is not considered unlocked until they have successfully entered their correct credentials. The number of previous incorrect logins has not been reset and further incorrect attempts will continue to be evaluated against them.
|
|
Disable password updates on locked accounts
|
Select this option to prevent users from initiating a password reset on their account until it has been manually unlocked.
|
Timeout
|
Session timeout by fixed time value
|
Enter the number of minutes or hours that a user session remains valid after sign-in, or 0 to disable fixed-time expirations.
|
|
Session timeout by fixed time unit
|
Select either Minutes or Hours to refer to the value in the previous setting.
|
|
Session timeout by inactivity value
|
Enter the number of minutes or hours that a session remains valid since the user was last active in OneLogin, or 0 to disable inactivity-based expirations.
|
|
Session timeout by inactivity unit
|
Select either Minutes or Hours to refer to the value in the previous setting.
|
|
Give users the "Keep me signed in" option on the login screen
|
Enable this setting to allow OneLogin sessions to persist after the browser closes.
Note: When this setting is enabled on any user policy, the "Keep me signed in" option appears on the login page for all users regardless of policy, but will only work for users who are assigned to a policy with the setting enabled.
|
MFA
Smart Access
|
Deny access if user meets or exceeds the selected risk level
|
Enable this setting to allow Smart Access to reject users' login attempts based on the risk level you select.
|
|
Risk level
|
Select the risk level that the login attempt must be evaluated below in order to pass Smart Access, with Low providing the strictest security and High providing the most relaxed user experience.
|
Important: All new users are typically considered High risk before the Vigilance AI risk engine has enough data to analyze the user's normal login behaviors. Because of this, it's necessary that you assign your new users to an onboarding user policy with Smart Access disabled.
If Smart Access is applied to a new user, their account may become locked out, permanently blocked, or disabled, requiring an admin escalation.
When the new user's typical login pattern has been established and their risk score lowers, you can then reassign them to their appropriate group's user policy moving forward.
Require trusted device
|
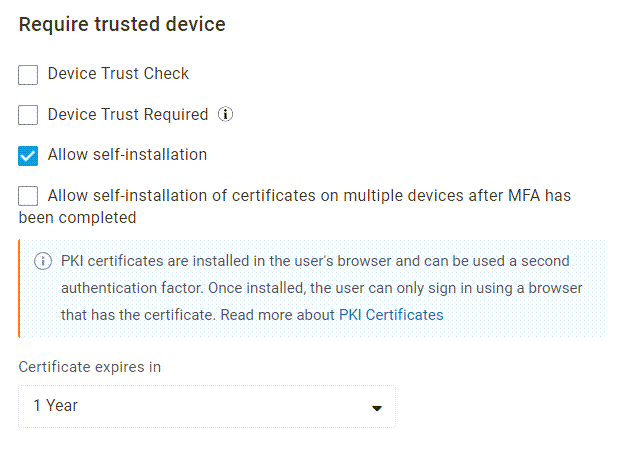
Device Trust Check
|
Enable this setting to check for a trusted device certificate upon login. Users are prompted for a certificate if one isn't found, but may still log in without submitting one unless Device Trust Required is also enabled.
Note: This setting must be enabled by your OneLogin account representative before it appears.
|
|
Device Trust Required
|
Enable this setting to require all users, including admins, to have a PKI certificate installed on their device in order to access OneLogin.
If this setting is enabled, be mindful that even the account owner may become locked out, requiring a call to OneLogin support to regain access to your tenant.
|
|
Allow self-installation
|
Enable this setting to allow users to install PKI certificates to their own device.
|
|
Allow self-installation of certificates on multiple devices after MFA has been completed
|
Enable this setting to allow users to install certificates to more than one device. Users must have MFA configured before they can install certificates to additional devices after their first.
Note: This setting must be enabled by your OneLogin account representative before it appears.
|
|
Certificate expires in
|
Select how long device certificates remain valid on a user's device. You can select from 1, 2, or 5 years.
|
Multi-Factor Authentication
|
Require MFA
|
Enable this setting to require all users assigned to this policy to sign in with a one-time password (OTP) generated by the authentication factors that you select.
|
|
Available factors
|
Select which of the authentication factors you've previously configured that you'd like to be available for MFA.
|
Disable OneLogin Protect push-notifications
|
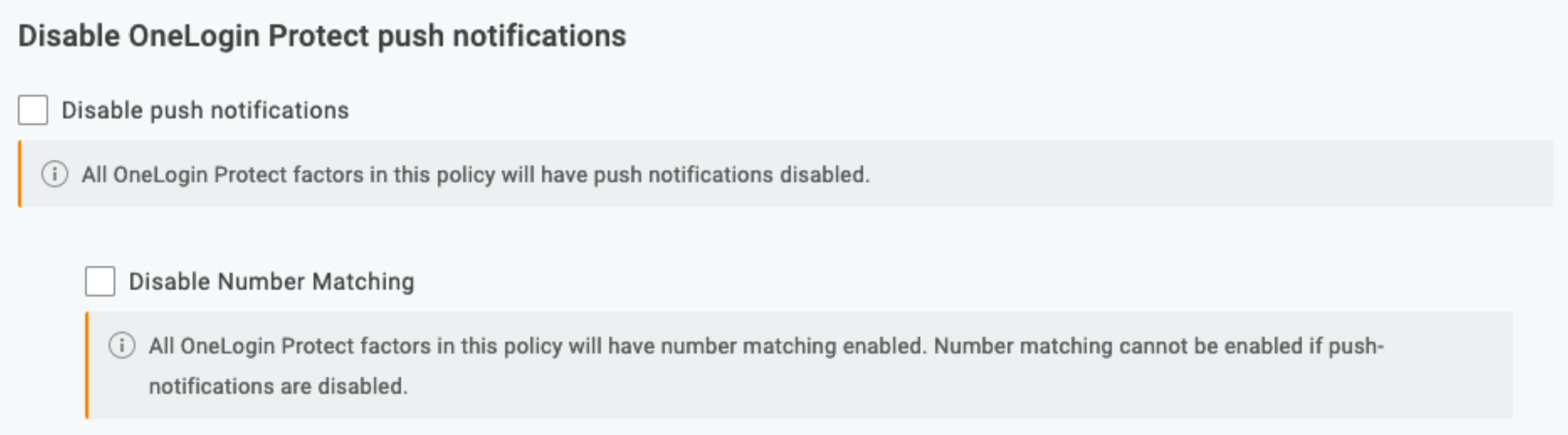
Disable push-notifications
|
When checked, OneLogin Protect push notifications will be disabled for authenticating user logins; this can help prevent a push-fatigue attack if the user's credentials are compromised. You can also choose to disable push notifications for unlocking user accounts in Account Recovery.
Important: If you have an app policy with OneLogin Protect MFA enabled, then disabling push notifications in the user policy will require users assigned to this policy to manually generate an OTP in their OneLogin Protect app, as the app will be unable to automatically use push notifications to request access.
|
|
Disable Number Matching
|
When checked, number matching will be disabled for authenticating user logins via push notification. If left unchecked, users are shown a random two-digit number on login attempt and prompted to enter the same number in their mobile device when accepting the push notification. This feature is not compatible with RADIUS.
|
Phone number for SMS
|
Allow user to change phone number for OneLogin SMS
|
If you have OneLogin SMS configured as an authentication factor, you can enable this setting to allow users to update the phone number used for their SMS verification by editing their user profile.
|
Email Configuration
|
Show email address hint in MFA prompt
|
If you have OneLogin Email configured as an authentication factor, you can enable this setting to provide users with a partial email address when prompting them for authentication. Only the first character of the username and last character of the email domain will be shown. For example, example@email.com would display as e*****@*****l.com.
|
MFA Device Registration
|
Users without a MFA device must register one before being able to login.
|
Select this option to require users on this policy to register a device for MFA in order to access OneLogin. If they don't already have one configured, they'll be immediately prompted to register one when they sign in.
|
|
Do not prompt users to register an MFA device during login
|
Select this option to allow users to sign in without having any MFA devices registered. They can still configure MFA devices in their OneLogin settings after sign-in.
This setting is unavailable if users are not permitted to manage MFA devices via their profile in MFA Device Management.
|
MFA Device Management
|
Allow users to manage MFA devices via Profile
|
Enable this setting to provide users the option to configure MFA devices via the OneLogin settings in their user profile.
If this setting is disabled, the option to disable the device registration prompt will be unavailable in MFA Device Registration. Since they will be unable to configure their devices later, users must register one before accessing OneLogin.
|
MFA Bypass
|
OTP bypassed for the following IP addresses
|
Enter one or more IP addresses to exempt from required OTP authorization; this is useful if you want to allow users easier access when signing in from specific on-site devices, but require additional security when accessing OneLogin remotely or using their personal devices. If entering multiple addresses, separate each with a single space.
|
|
Ignore X-Forwarded-For header IP addresses
|
This setting is enabled by default. Disable it to require OneLogin to evaluate IP addresses from the X-Forwarded-For header in addition to the gateway IP address.
|
|
MFA Bypass for Trusted Device
|
Enable this setting to allow users to sign in without using any additional authentication factors when they're accessing OneLogin from a device with a PKI or third-party certificate, or using OneLogin Desktop.
|
Enforcement Settings
|
OTP required for
|
Select whether to require OTP authentication only for users with admin access, for any user who has been configured for OTP, or for all users regardless of their access level or OTP configuration.
|
|
OTP required at
|
Select whether to require OTP authentication at every login or only during the first login from an unknown browser.
|
|
Security cookie expiration
|
Select the number of days that a OneLogin security cookie will remain valid and treat the user's browser as a known device. After this time passes, the cookie will expire and the user will be required to authenticate via OTP again.
|
Note: The user must accept browser cookies in order for OneLogin to recognize their browser for security enforcement. If OTP is required for unknown browsers and the user does not accept cookies, they will be prompted for OTP authentication each time they sign in.
Smart MFA
|
Suppress if risk is equal to or lesser than
|
Enable this setting to allow Smart MFA to exempt users from MFA requirements based on the risk level you select.
|
|
Risk level
|
Select the maximum risk level to allow to bypass MFA requirements, with Minimal providing the strictest security and Very High providing the most relaxed user experience.
|
IP Addresses
IP address allow list
Important: This setting provides the strictest degree of security for your OneLogin users. If any IP addresses are entered here, then all users attempting to use OneLogin via any other IP address will be denied access.
|
Allowed IP addresses
|
Enter one or more IP addresses to permit access to OneLogin, or leave blank to allow users to sign in regardless of their IP address. If entering multiple addresses, separate each with a single space.
|
|
Ignore X-Forwarded-For header IP addresses
|
This setting is enabled by default. Disable it to require OneLogin to evaluate IP addresses from the X-Forwarded-For header in addition to the gateway IP address.
|
|
MFA Bypass for Trusted Device
|
Enable this setting to allow users to sign in without using any additional authentication factors when they're accessing OneLogin from a device with a PKI or third-party certificate, or using OneLogin Desktop.
|
Customization
System Use Notification
Enable this setting to enter a custom system use notification that will be shown before each login, such as a warning, disclaimer, or message broadcast, which the user must accept before proceeding.
This is similar to the Terms and Conditions option, but while the Terms and Conditions will appear only during a user's first login, the system use notification must be accepted every time a user on this policy accesses OneLogin.
|