Many network appliances can be configured to use a RADIUS server for user authentication. For example, when a user establishes an IPsec VPN using their desktop VPN client, the network appliance can send an Access-Request to a RADIUS server, which authenticates the entered credentials against a user store. OneLogin provides a RADIUS configuration for processing these authentication requests. When OneLogin receives a RADIUS Access-Request message, the user's credentials are authenticated against the directory linked to the user.

Configuring OneLogin's RADIUS Server Interface
Take a look at this brief training video to learn more about RADIUS and how to configure it with OneLogin.
Watch Now
Prerequisites
- A Network Access Server (NAS) device supporting the RADIUS protocol with PAP, EAP-TTLS/PAP, or EAP-PEAP/MSCHAPv2, e.g.:
- Cisco ASA
- Fortinet 200B
- Juniper SSL VPN
Note: Other RADIUS authentication methods such as MS-CHAP, MSCHAPv2 (without EAP-PEAP), and EAP-TLS are not currently supported.
- Administrative access to and familiarity with the RADIUS protocol configuration in your NAS
- Access to your NAS IP address and shared secret
- A unique routable IP address for each individual RADIUS configuration
RADIUS Configuration
In your OneLogin admin portal, go to Authentication > RADIUS and click New Configuration or select an existing configuration.
Configurations
|
Secret
|
Enter a secret string as shared with your NAS.
- Shared secrets may be up to 30 characters and include the following special characters:
~ ! @ # $ % ^ & * ( ) - _ = + [ ] { } \ | / ? < > , . ; : ' "
- When creating a brand new shared secret, please allow up to an hour for the secret to be cached and usable.
|
|
IP Addresses
|
Enter one or more internet-routable IP addresses or ranges for your NAS, separated by spaces.
|
|
Roles Restriction
|
If desired, select a role in OneLogin to restrict access to only members of that role.
|
Login challenge
If your NAS supports two-step authentication, you may select Require OTP verification as a 2nd step to require users to provide a temporary one-time passcode (OTP) after entering their username and password, then choose whether to apply the requirement to all users or only those whose security policy already requires an OTP authentication.
You may instead prefer to incorporate OTP verification in a single step by requiring users to enter the code concatenated with their password. In this case, leave Require OTP verification as a 2nd step unselected and choose OTP+Password when configuring Credentials below.
If 2nd-step OTP verification is required, your NAS must support Access-Challenge with untunnelled PAP authentication, and users must register their OTP device in their OneLogin profile with one of the following OTP providers:
This option is not supported by the EAP-PEAP/MSCHAPv2 authentication method. RADIUS is not compatible with OTP number matching.
Password
|
Enable Password Expiration Policy Enforcement
|
Enable this setting to have the OneLogin RADIUS server enforce the password expiration configured in the user's security policy.
|
|
Enable NT hash for EAP-PEAP/MSCHAPv2
|
If using EAP-PEAP/MSCHAPv2 authentication, enable this setting to allow OneLogin to store an NT hash of the user's password. Users must log in or reset their OneLogin password at least once before the NT hash is captured and available to use.
|
Credentials
If creating a new RADIUS configuration, Save the configuration in order to access these settings.
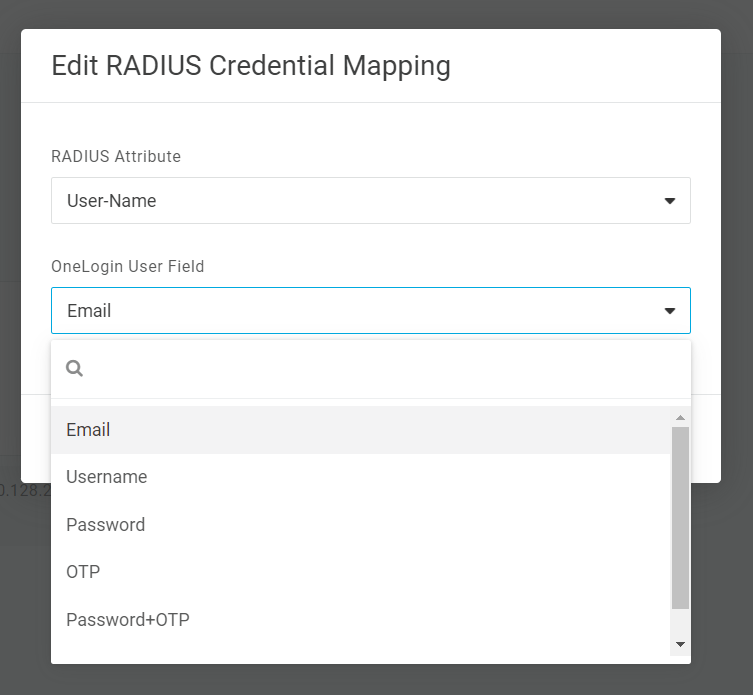
By default, the user's User-Name attribute in RADIUS is mapped to the Email attribute in their OneLogin record, with their RADIUS User-Password mapped to their OneLogin Password. If preferred, you may select either mapping and choose a different OneLogin attribute to act as the user's credentials.
|
User-Name
|
|
Email
|
(Default) The user's email address as stored in their OneLogin user record
|
|
Username
|
The user's username as stored in their OneLogin user record
|
|
SAMAccountName
|
The user's sAMAccountName as synced from Active Directory to their OneLogin user record
|
|
User-Password
|
|
Password
|
(Default) The user enters only their OneLogin password in the password field.
This option may be combined with a second prompt for OTP verification if enabled in your Login challenge settings.
|
|
OTP
|
The user enters only the temporary passcode generated by an OTP provider in the password field.
If this option is enabled, the user does not enter their OneLogin password at any stage of RADIUS authentication. This can be useful in RADIUS implementations that ues PAP only as it bypasses any vulnerabilities caused by compromised passswords.
|
|
Password+OTP
|
The user enters both their password and OTP concatenated together. For example, if the user's password is P@ssw0rd! and the code generated by their OTP provider is 123456, they must enter P@ssw0rd!123456 in the password field.
|
Attributes
This setting is only enabled by request. Contact your OneLogin account manager to allow access to this configuration.
If necessary, you can set your OneLogin RADIUS configuration to return a vendor-specific attribute (VSA) found in the FreeRADIUS Dictionary or some standard attributes, such as Filter-ID attribute 11, with the RADIUS Access-Accept message.
Click Add Attribute or select a previously configured attribute to edit or remove it.
|
Attribute has dynamic group value
|
Leave this setting disabled for a static attribute value, or enable it to dynamically match the attribute based on OneLogin roles.
|
|
RADIUS Attribute Name
|
Enter the RADIUS attribute's name.
Name matching is not case sensitive. If the VSAs return unexpected results, please check your NAS documentation to verify that the names and values are entered correctly.
|
|
RADIUS Attribute Value
|
If using a static attribute, enter its value.
|
|
Roles to match
|
If using a dynamic attribute, select one or more roles to match to the attribute's value.
|
|
Use a delimiter
|
By default, multiple values for dynamic attributes are delimited by spaces. If preferred, you may enter an alternate delimiter, such as a comma or semicolon.
|
Best Practice: After configuring your attributes, we strongly recommend using a RADIUS test client such as radtest to verify that the attributes you expect are returned with the Access-Accept message.
NAS Configuration
After completing your RADIUS configuration in OneLogin, use the following settings for your OneLogin region to complete configuration with your NAS. Consult your NAS documentation for configuration details.
|
NAS Configuration
|
OneLogin - US
|
OneLogin - EU
|
|
AAA/RADIUS Primary Server
|
Domain: radius.us.onelogin.com
IP: 23.183.113.15
|
Domain: radius.eu.onelogin.com
IP: 23.183.113.18
|
|
AAA/RADIUS Secondary Server
|
Domain: radius2.us.onelogin.com
IP: 23.183.112.15
|
Domain: radius2.eu.onelogin.com
IP: 23.183.112.18
|
|
Authentication Scheme
|
PAP or EAP-TTLS/PAP
|
|
RADIUS Port
|
UDP/1812
|
|
Secret/Key
|
Enter the Secret string from your OneLogin configuration.
|
Best Practice: When possible, use the RADIUS server domain name rather than the IP address, as IP addresses are more likely to change over time. |