The applications you use with OneLogin all have unique purposes, features, and users, which means they all have unique security requirements to make sure your organization has the best balance of protection and user-friendliness to meet your needs. Using app policies, you can tailor your users' authentication and access settings on an app-by-app basis with multi-factor authentication, allowed IP addresses, and more.
App Policy Management
Creating an App Policy
-
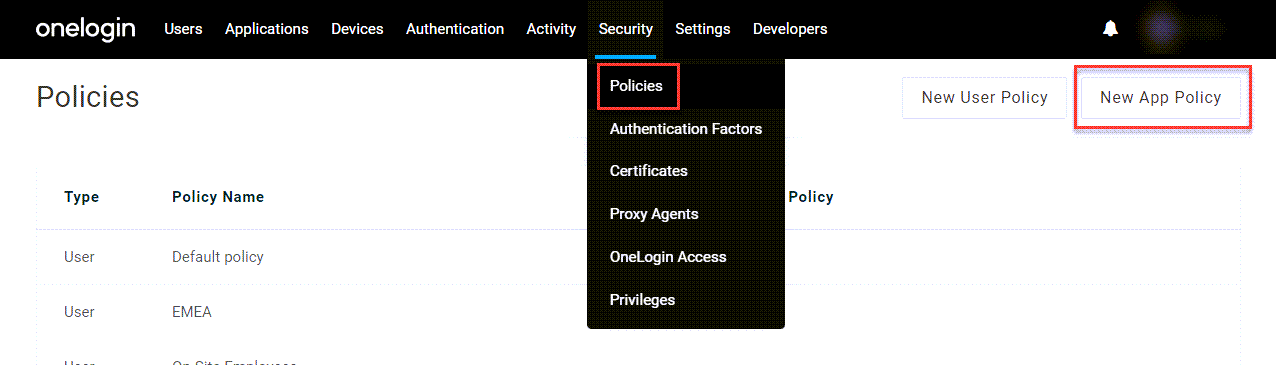
In your OneLogin admin portal, go to Security > Policies and click New App Policy.
-
Give the policy a descriptive name and click Save.

Assigning an App Policy
From your app management, select an application and go to Access. Under Policy, select the policy you want to assign to this app. The policy will be applied to all users of the application.
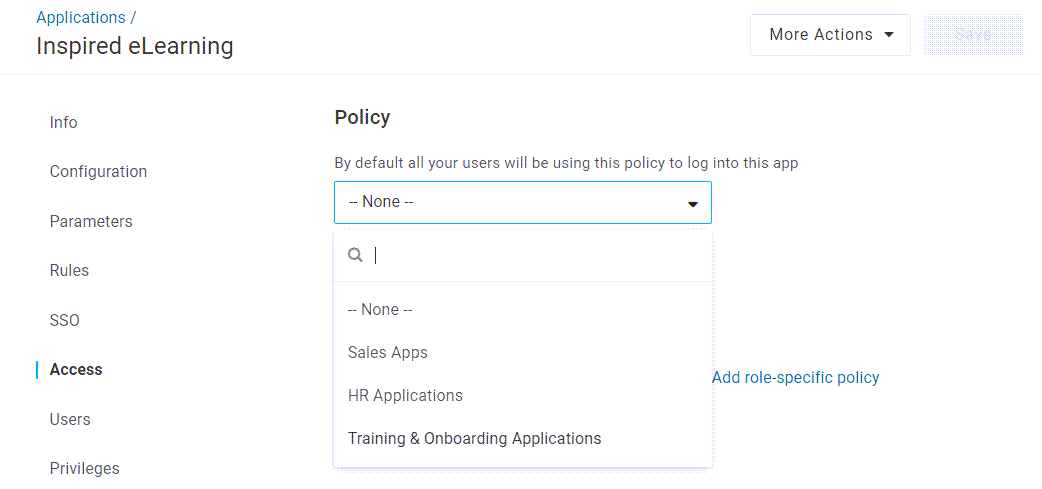
Role-Based Policies
Role-based policies allow you to provide different security requirements for only some users of an application. For example, you might want to implement tighter security requirements for users who have more powerful access within that app, or create exceptions for new employees who haven't yet obtained some of their security credentials.
-
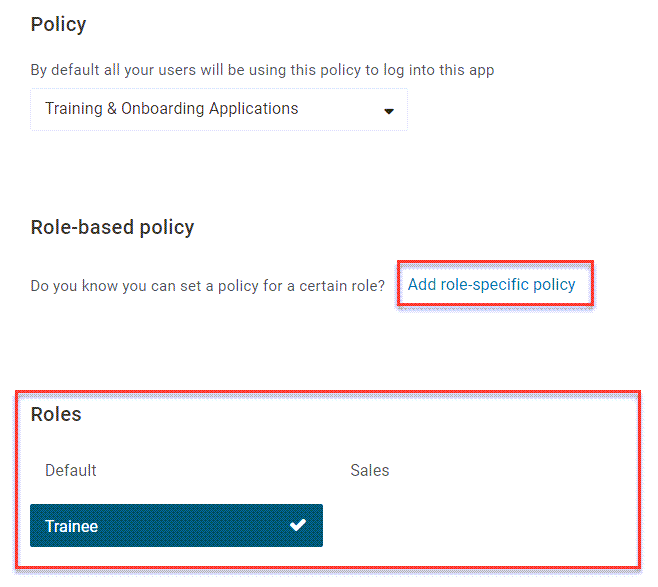
Ensure the appropriate role has been enabled under Roles and click Add role-specific policy.
-
Select the appropriate role and policy. The role you select will now have the access requirements specified by that policy, while all other users will continue to use the requirements of the policy assigned under Policy.
![[Role] will use [Policy]](https://s3.amazonaws.com/onelogin-screenshots/admin/security/policies/app/role-policy.png)
Deleting an App Policy
To remove an existing app policy, open the policy and click Delete.

App Policy Settings
IP Address Allow List
|
Allowed IP addresses
|
Enter a list of IP addresses that are allowed to access apps using this policy, or leave blank to allow access from any IP address.
|
|
Ignore X-Forwarded-For header IP addresses
|
Enable this setting to prevent OneLogin from evaluating IP addresses from the X-Forwarded-For header.
|
Smart Access
This feature requires a OneLogin subscription that includes SmartFactor Authentication. Speak with your account representative for more information.
|
Deny access if user meets or exceeds the selected risk level
|
Enable this setting to allow Smart Access to reject users' login attempts based on the risk level you select.
|
|
Risk level
|
Select the risk level that the login attempt must be evaluated below in order to pass Smart Access, with Low providing the strictest security and High providing the most relaxed user experience.
|
Important: All new users are typically considered High risk before the Vigilance AI risk engine has enough data to analyze the user's normal login behaviors. Because of this, it's necessary that app policies with Smart Access enabled are never applied to new users. You can use Role-Based Policies to provide exceptions for new users to access apps that typically require Smart Access.
If Smart Access is applied to a new user, their account may become locked out, permanently blocked, or disabled, requiring an admin escalation.
Forced Authentication or Skip User Policy MFA
Enable Forced Authentication to prompt users to re-enter their authentication credentials when they try to access apps with this policy, even when they're already signed in to OneLogin. You can also provide users with a grace period that overrides forced authentication if they already authenticated their accounts within that time period. For example, if you select 60 seconds, users who signed in less a than a minute ago won't be required to reauthenticate. The minimum grace period is 3 seconds, to prevent authentication loops.
Require trusted device
|
Browser Certificate Required
|
Enable this setting to require all users, including admins, to have a PKI certificate installed on their device in order to access OneLogin.
If this setting is enabled, be mindful that even the account owner may become locked out, requiring a call to OneLogin support to regain access to your tenant.
|
|
3rd Party Certificates Enabled
|
Enable this setting to use third-party certificates with OneLogin's existing PKI certificate structure to check for device trust.
Note: This setting must be enabled by your OneLogin account representative before it appears.
|
Multi-Factor
Enable this setting to require users to authenticate with multi-factor authentication (MFA) when accessing apps with this policy.
Choose Require MFA to allow any MFA factors to be used for authentication.
Choose Specify Acceptable MFA Factors to allow only the factors you specify to be used as authentication. If the user already authenticated with one of these factors when signing into OneLogin, they will not be prompted for it again unless forced authentication has also been enabled. If they did not use MFA, or used a factor not specified by this policy, they'll be prompted to authenticate when accessing the app.
MFA Bypass
|
Bypass MFA for the following addresses
|
Enter a list of IP addresses that can bypass MFA requirements to access the apps associated with the policy.
|
|
Ignore X-Forwarded-For header IP addresses
|
This setting is enabled by default. Disable it to require OneLogin to evaluate IP addresses from the X-Forwarded-For header in addition to the gateway IP address.
|
|
Skip if OTP received within last 00 minutes
|
Enable this setting to allow users to bypass MFA if they have already performed MFA when accessing OneLogin within the amount of time you specify.
|
|