|
This article describes how to set up OneLogin's LDAP Directory Connector 2 (LDC) to synchronize users between your LDAP directory and OneLogin and authenticate OneLogin users against your LDAP directory.
Prerequisites
Server Requirements
-
The LDC is compatible with LDAPv3 compliant directory servers. It has been tested with the following LDAP Directory Servers:
- OpenLDAP version 2.4
- PingDirectory Server
- Apache DS
- Microsoft Active Directory Lightweight Directory Services (AD LDS): Windows Server 2012, 2016
The following servers have not been tested, but are expected to perform correctly with the LDC:
- Oracle Internet Directory
- Oracle Unified Directory
- IBM Security Directory Server
- NetIQ eDirectory
- CA Directory
- Red Hat Directory Server
- 389 Directory Server
Contact OneLogin customer support with any questions about your server needs.
- The directory connector accesses directory schema metadata to provide access to user attributes, although operational attributes and other intrinsic attributes specific to certain directory servers may not be accessible, and supports the following group schemas:
- Static groups with object classes, e.g.
groupOfUniqueNames, groupOfNames, and posixGroup
- AD LDS nested groups with potentially nested Group memberOf references
- OpenLDAP memberOf overlay dynamic groups, in which each user's group membership is searched from the LDAP user entry and returned as a set of memberOf attribute values, one for each unique Group distinguished name
- VLDAP Roles and Groups with
gidNumber on their attributes and posixGroup on its objectClasses, following RFC2307(bis) protocol
Host Machine Requirements
- Oracle Java Runtime Environment (JRE) 8 or OpenJDK 8 can be used with the directory connector.
-
CPU and RAM requirements may vary depending on your user count and server load. We recommend the following minimum specifications:
|
Users
|
vCPU
|
RAM
|
|
1-5,000
|
2
|
2 GB
|
|
5,000-100,0000
|
4
|
4 GB
|
|
100,000-1,000,000
|
8
|
8 GB
|
|
1,000,000-2,000,000
|
16
|
16 GB
|
|
2,000,000+
|
32
|
16 GB
|
Installing an LDAP Directory Connector
-
Go to Users > Directories and add a New Directory. Choose LDAP via Connector, enter a name for the directory in the title field, and Save the directory to enable additional configuration options.

-
A single LDC instance is created by default. You may later choose to Add LDAP Connector Instance if configuring multiple LDAP connectors for high availability, but for now, select your first connector instance to view its details.

- Enter a descriptive Name for the connector.
- Enter your LDAP domain controller's Hostname or IP address.
- Enter a Port for the domain controller (DC).
- Copy the Installation Token for use during the installation.
- Download the LDC installation file.
-
Extract and install the LDC to your desired host machine according to the steps provided in the included README file and edit its configuration file to add the installation token copied from OneLogin.
Only the installation token is required. All other configuration settings are optional. They may be configured now, or disregarded for a default installation.
-
Start the LDC using start-ldc.bat (Windows) or start-ldc.sh (Linux/Unix/OS X).
-
Return to the new directory in your OneLogin admin portal and refresh the page. If the LDC has succesfully connected to your OneLogin account and started running, its connector instance now displays ● Connected and additional configuration pages appear in the left sidebar.
-
Go to Connection and enter the additional connection details required for OneLogin to connect to your LDAP server:
|
Bind DN
|
The admin DN you use to connect to your LDAP server
|
|
Password
|
The password you use to identify the admin Bind DN
|
|
Authentication attribute
|
The LDAP attribute that your users will enter as their username on OneLogin's login page
|
|
UUID Attribute
|
The LDAP attribute that you use to uniquely identify your users
|
|
Base DN
|
The LDAP attribute that is used as the root context DN of your LDAP directory
|
Important: The fields used as your authentication and UUID attributes must be indexed in your LDAP server in order to prevent issues with authenticating users through the connector. See your server provider's documentation for more information.
-
Go to OU Selection to select the organizational units (OUs) you want to import to OneLogin.
Note: It may take several seconds to retrieve your directory's OU tree. If the tree does not appear, wait two minutes and refresh the page.
-
Save your changes; the directory connector is now configured to sync your selected OUs with OneLogin according to the default configuration. Go to More Actions > Synchronize to begin your first import, or install additional connectors for failover availability.
Configuring an LDAP Directory Connector
Directory Mappings
By default, OneLogin maps several directory attributes to be imported when users are synced with your LDAP directory. If preferred, you can add to or modify these default mappings.
This feature requires a OneLogin subscription that includes Advanced Directory. Speak with your account representative for more information.
Adding Custom Mappings
If you'd like to map a custom user field in OneLogin to your LDAP directory, click + to add a new row to your mappings and select the appropriate attributes from the dropdown menus provided.
Tip! Did you know it's possible to synchronize users' status from your LDAP directory to OneLogin too?
-
Map the LDAP status attribute to a custom OneLogin field.
-
Enable mappings in your advanced configuration.
-
Go to your OneLogin user mappings and create two new mappings for your custom field: one to deactivate and another to activate your users.
Modifying Sync Directions
By default, all directory mappings are inbound from your LDAP directory, meaning that the directory owns all field values and sends these to override the corresponding values in OneLogin. If you have Exporting users enabled in your advanced LDC settings, you can select the arrows in the Import/Export column to change some or all of your user fields to an outbound mapping, allowing OneLogin to provision these attributes to the LDAP directory instead.
Note: If you wish to enable LDAP user deletion in your configuration file, all attributes must be configured for outbound mapping.
Advanced Settings
Go to Advanced to manage additional features and settings:
|
Enable mappings
|
This feature allows you to use OneLogin's user mappings to automatically control your users' access to apps, groups, or roles.
Note: This is not to be confused with the directory mappings configured in the previous section.
|
|
Stage users
|
This feature allows you to choose which users in your LDAP directory are synchronized to OneLogin before import. If disabled, OneLogin will import all users from your directory automatically.
|
|
Exporting users
|
This feature allows you to reverse the usual sync direction and instead provision users and user attribute updates from OneLogin to your LDAP directory.
|
|
Deleted users in LDAP Directory...
|
Select how you would like OneLogin to handle users who have been deleted from your LDAP directory: they can be automatically deleted in OneLogin as well, or left unaffected.
Note: This setting presumes that you are using a traditional inbound configuration. If you are provisioning users from OneLogin to the directory and wish deleted users in OneLogin to be deleted in the directory as well, you must ensure that all attributes are configured for export in your directory mappings and ldc.ldap.delete=true in your LDC installation's configuration file.
|
|
Enable Smart Password
|
With Smart Password, OneLogin is able to sync password changes to the LDAP directory, effectively allowing OneLogin to act as your primary password manager.
If you are syncing with multiple directories, Smart Password can also be used to synchronize passwords from another directory into your LDAP directory. In this event, OneLogin acts as the middleman between the two directories and does not store any user passwords.
|
|
Enforce OneLogin password expiration policies
|
This feature enables OneLogin to ensure that the LDAP directory adheres to the password expiration settings you've configured in your OneLogin security policies. When enabled, the most restrictive policy applies; if your LDAP directory requires more frequent password updates than OneLogin, it will continue to apply its own policy for shorter password intervals.
|
Installation Files
The installation contains two configuration files:
conf/ldc-default.conf — The factory default configuration settings. Do not edit this file.conf/ldc.conf — The site-specific configuration. This file may be edited with your preferred settings.
When the LDC is started, it first loads the conf/ldc-default.conf configuration, then overrides these settings with any located in conf/ldc.conf. By default, the conf/ldc.conf file contains only the most commonly customized settings, but you can customize additional settings by copying them in from conf/ldc-default.conf.
|
ldc.api.token
|
Required. Paste the Installation Token copied from the connector instance configuration.
|
|
ldc.api.location
|
Enter US, EU, or DE to idicate the location where your OneLogin directory is hosted, which selects the API endpoint URLs used.
Default: US
|
|
ldc.sync.interval
|
Enter a synchronization wait interval between 15 seconds and 86,400 seconds (24 hours); this is how long the connector will wait after syncing user changes and before checking for new changes to sync.
Default: 60
|
|
ldc.sync.threads
|
Enter the maximum number of concurrent threads between 5 and 20 threads (combined) to use when inserting/updating/deleting OneLogin users via HTTP calls to OneLogin APIs.
Default: 10
|
|
ldc.ldap.ssl
|
Enable or disable forced use of SSL/TLS connections between the LDAP Directory Connector and the LDAP directory server.
Important: Your LDAP directory server must be configured for and listening for secure SSL/TLS connections.
Default: false
|
|
ldc.ldap.delete
|
Enable or disable LDAP user deletion.
An LDAP user can only be deleted if the associated OneLogin directory field mappings are all outbound and Exporting users is enabled in the LDC's advanced configuration.
Default: false
|
|
ldc.ldap.us
|
Enter a list of the LDAP objectClasses used to search for user LDAP entries within the selected organizational units.
Default: person,organizationalPerson,inetOrgPerson
|
|
ldc.ldap.uc
|
Enter a list of the LDAP objectClasses added to an entry when a new user entry is created in the LDAP directory. This value is used when user provisioning is enabled and a new user is created in the LDAP directory based on a user that exists in the OneLogin directory.
Default: top,person,organizationalPerson,inetOrgPerson
|
|
ldc.ldap.user.scan.search.filter
|
Use this value to modify the base LDAP user search filter, which searches for LDAP entries with any of the registered user object classes. For example, you might enter ldc.ldap.user.scan.search.filter=(mail=*@example.com) to include only LDAP entries with an email addresses ending in 'example.com' or ldc.ldap.user.scan.search.filter=(!(mail=*@example.com)) to exclude all such entries.
|
|
ldc.ldap.search.paging.enabled
|
Enable or disable paging of LDAP search results. It may be necessary to enable this in some LDAP directory servers that return exception failures if a search exceeds maximm search results. This option can also be beneficial in reducing the maximum amount of heap memory needed by your environment.
Default: false
|
|
ldc.ldap.search.paging.size
|
Enter 1-1000 to indicate the maximum search results returned in a page when search paging is enabled.
This property has no effect unless ldc.ldap.search.paging.enabled=true.
Default: 1000
|
|
ldc.ldap.group.search.type
|
Enter one of the following group search types:
|
Default: none
|
No group membership searches are performed.
|
|
adlds-nested
|
Microsoft AD LDS nested group membership searches
|
|
static-groups
|
Static group membership searches
|
|
openldap-memberof
|
OpenLDAP memberOf overlay group membership searches
|
|
|
ldc.ldap.group.service.none.factory.class
|
Do not change this value.
This property indicates the Java class used to create the GroupService when ldc.ldap.group.search.type=none.
Default: com.onelogin.ldc.ldap.NoOpGroupServiceFactory
|
|
ldc.ldap.group.service.none.config.debug
|
Enable or disable DEBUG-level logging from the group service when ldc.ldap.group.search.type=none.
Default: false
|
|
ldc.ldap.group.service.adlds-nested.factory.class
|
Do not change this value.
This property indicates the Java class used to create the GroupService for AD LDS nested group types using the Group object class when ldc.ldap.group.search.type=adlds-nested.
Default: com.onelogin.ldc.ldap.AdLdsNestedGroupServiceFactory
|
|
ldc.ldap.group.service.adlds-nested.config.debug
|
Enable or disable DEBUG-level logging from the group service when ldc.ldap.group.search.type=adlds-nested.
Default: false
|
|
ldc.ldap.group.service.adlds-nested.config.cache-enabled
|
Enable this property to increase performance by preloading internal LDC data structures with nested AD LDS group relationships.
Default: false
|
|
ldc.ldap.group.service.adlds-nested.config.cache-reload-each-sync-pass
|
Enable or disable the group cache to reload on every synchronization pass. When disabled, the cached group information is not reloaded until the LDC is restarted or reconfigured or a manual synchronization command is issued.
This property has no effect unless ldc.ldap.group.service.adlds-nested.config.cache-enabled=true.
Default: true
|
|
ldc.ldap.group.service.static-group.factory.class
|
Do not change this value.
This property indicates the Java class used to create the GroupService for static group types when ldc.ldap.group.search.type=static-groups.
Default: com.onelogin.ldc.ldap.StaticGroupServiceFactory
|
|
ldc.ldap.group.service.static-groups.config.debug
|
Enable or disable DEBUG-level logging from the group service when ldc.ldap.group.search.type=static-groups.
Default: false
|
|
ldc.ldap.group.service.static-groups.config.classes
|
Enter the static group object classes that GroupService searches for when it looks for and assigns user group memberships. All three values are listed by default, but you can remove unneeded object classes to improve performance.
Default: groupofuniquenames,groupofnames,posixgroup
|
|
ldc.ldap.group.service.static-groups.config.cache-enabled
|
Enable this property to increase performance by preloading internal LDC data structures with static groups.
Default: false
|
|
ldc.ldap.group.service.static-groups.config.cache-reload-each-sync-pass
|
Enable or disable the group cache to reload on every synchronization pass. When disabled, the cached group information is not reloaded until the LDC is restarted or reconfigured or a manual synchronization command is issued.
This property has no effect unless ldc.ldap.group.service.static-groups.config.cache-enabled=true.
Default: true
|
|
ldc.ldap.group.service.openldap-memberof.factory.class
|
Do not change this value.
This group service searches for the memberOf attribute of a user's LDAP entry and relies on the installed OpenLDAP memberOf overlay to resolve the group DNs, and therefore does not currently provide any group membership caching.
Default: com.onelogin.ldc.ldap.OpenLdapMemberOfGroupServiceFactory
|
|
ldc.ldap.group.service.openldap-memberof.config.debug
|
Enable or disable DEBUG-level logging from the group service when ldc.ldap.group.search.type=openldap-memberof.
Default: false
|
|
ldc.ldap.user.password.hash.algorithm
|
Set the user password message digest (hash) algorithm supported by your LDAP server to be used for password reset and change requests:
|
Default: CLEARTEXT
|
Send the cleartext user password to the LDAP server. The password will either be stored in cleartext or automatically hashed according to your LDAP server's password policy settings.
Use this value if your LDAP server automatically hashes passwords.
|
|
SHA
|
Use the unsalted SHA-1 message digest algorithm. The cleartext password will be hashed by the LDAP connector using the SHA-1 algorithm, then base-64 encoded and prepended with the tag {SHA}.
|
|
SSHA
|
Use the salted SHA-1 message digest algorithm. The cleartext password will be appended with 8 bytes of random data and the resulting value will be hashed by the LDAP connector using SHA-1, then base-64 encoded and prepended with the tag {SSHA}.
|
|
|
ldc.ldap.user.password.modify.rfc3062.enabled
|
Enable or disable the option to modify/reset passwords using the RFC 3062: LDAP Password Modify Extended Operation.
This extension is not available in all LDAP server environments, so check your server features before enabling.
If enabling this extension with an OpenLDAP server, ensure that ldc.ldap.user.password.hash.algorithm=CLEARTEXT.
Default: false
|
|
ldc.ldap.admin.bind.dn
|
If you prefer to keep the LDAP server admin login credentials under your own security, set the LDAP server admin bind DN here.
Note: Setting this value overrides the admin bind DN configured in the LDAP Directory Connector cloud configuration. You may either leave the cloud-based value blank or enter fake values.
|
|
ldc.ldap.admin.bind.password
|
If you prefer to keep the LDAP server admin login credentials under your own security, set the LDAP server admin bind password here.
Note: Setting this value overrides the admin bind password configured in the LDAP Directory Connector cloud configuration. You may either leave the cloud-based value blank or enter fake values.
|
|
ldc.admin.server.port
|
Enter the TCP port number on which the LDAP Connector Admin HTTP Server listens for connections.
Default: 8111
|
|
ldc.proxy.enabled
|
Enable or disable LDC connectivity to remote OneLogin services through a specified outgoing HTTP/HTTPS proxy server.
Default: false
|
|
ldc.proxy.host
|
Enter the IP address or hostname of the proxy server.
Default: 127.0.0.1
|
|
ldc.proxy.port
|
Enter the TCP port number on which the proxy server accepts connections for HTTP/HTTPS clients.
Default: 3128
|
|
ldc.proxy.auth.type
|
Enter none, basic, or ntlm to indicate the authentication type the LDAP Directory Connector should attempt with the proxy server.
Default: none
|
|
ldc.proxy.auth.basic.username
|
Enter the username to be used for proxy authentication when ldc.proxy.auth.type=basic.
|
|
ldc.proxy.auth.basic.password
|
Enter the password to be used for proxy authentication when ldc.proxy.auth.type=basic.
|
|
ldc.proxy.auth.ntlm.username
|
Enter the username to be used for proxy authentication when ldc.proxy.auth.type=ntlm.
|
|
ldc.proxy.auth.ntlm.password
|
Enter the password to be used for proxy authentication when ldc.proxy.auth.type=ntlm.
|
|
ldc.proxy.auth.ntlm.domain
|
Enter the domain to be used for proxy authentication when ldc.proxy.auth.type=ntlm.
|
|
ldc.proxy.auth.ntlm.workstation
|
Enter the name of the workstation to be used for proxy authentication when ldc.proxy.auth.type=ntlm.
|
|
ldc.debug.verbose
|
Enable or disable verbose logging when DEBUG-level logging is configured.
Enabling this property may negatively impact performance and memory use.
Default: false
|
|
ldc.ldap.extra.attributes
|
This value is combined with the LDAP attributes discovered by the LDC and sent to the server to be used with directory mappings. It's included during synchronization and used to configure custom attributes that aren't discovered by the LDC.
|
Secure Properties
Some configuration properties, like passwords, must be secured in your configuration file. These can be encrypted by using the secure-properties utility.
-
Add the SECURE_PASSWORD environment variable to your conf/ldc.conf file with the password to be used for encrypting and decrypting properties.
E.g., SECURE_PASSWORD=ABC(1DefGHiJk2lm3NOp4QrSTU5vW6XYZabcDEfGHI7jK8l=).
-
Run the script ./bin/secure-properties.sh (Linux/Unix/OS X) or .\bin\secure-properties.bat (Windows).
-
Introduce the value to be encrypted.
-
Copy the encrypted value to the configuration property that requires additional security.
Starting and Stopping an LDAP Directory Connector
Best Practice: We recommend enabling Directory Fallback Password Cache in your account settings to prevent an outage in the event that all connectors experience disconnection, as well as configuring multiple LDC instances for failover purposes and enabling automatic failover in your directory's Advanced settings.
To monitor the status of any directories you have configured, go to Users > Directories in your OneLogin admin portal and select the directory to view details about its connectors. Any failed LDC instances will display a ⬤ Disconnected indicator.
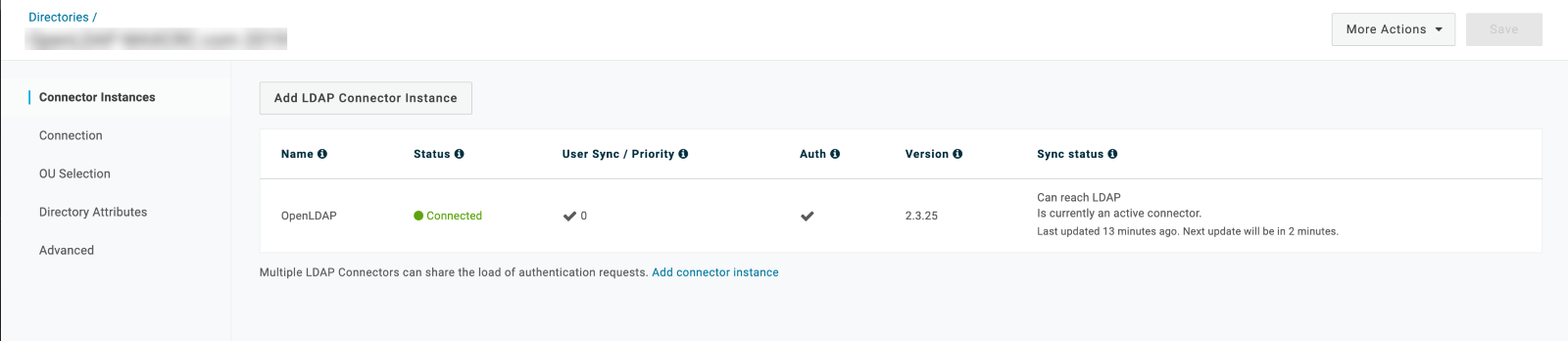
Starting the Connector
The connector can be started as either a foreground or a background process, depending on your needs. When you first configure the LDC, you may wish to start it in the foreground in order to see errors and enable fast stopping. Once you've completed deployment and testing, you may change it to a background process to allow it to continue running as necessary.
In Windows, edit the text file start-ldc.bat in the bat folder, or in Linux/Unix/OS X, edit start-ldc.sh in the bin folder. In this file, set the environment variable BACKGROUND to either "true" or "false". When the script is run in the foreground, console messages will be displayed in the command window. When run in the background, they will be directed to .\logs\ldc_console.log.
Tuning Starting Performance
The start file can also be modified for optimal connector performance based on the number of users syncing between OneLogin and your LDAP directory. Edit the file's JVM_OPT values to the following recommended settings:
Contact OneLogin for recommendations if you are actively synchronizing more than 2,000,000 users between your directories.
|
Synchronized Users
|
Java Virtual Machine
|
|
1-10,000
|
-Xms512M
|
|
10,000-50,0000
|
-Xms1g
|
|
50,000-100,000
|
-Xms2g
|
|
100,000-1,000,000
|
-Xms4g
|
|
1,000,000-1,500,000
|
-Xms6g
|
|
1,500,000-2,000,000
|
-Xms8g
|
Stopping the Connector
If necessary, it is possible to hard-stop the connector by killing the Java Process ID in Linux/Unix/Mac OS X, or by ending the Java process in the Windows Task Manager. However, we recommend stopping the connector gracefully whenever possible so that it is able to notify OneLogin cloud services of associated connection, monitoring state, and failover state updates. This can be done with the commands $ ./bin/stop-ldc.sh (Linux/Unix/Mac OS X) or > .\bin\stop-ldc.bat (Windows).
Upgrading an LDAP Directory Connector
-
Gracefully stop the existing installation and copy its conf/ldc.conf configuration file to a secure location. Uninstall the previous connector.
-
In your OneLogin admin portal, open the LDC instance and verify that its Installation Token matches that stored in your configuration file. Download the new installation file.
-
Extract and install the new installation as normal, and replace its conf/ldc.conf with your previous configuration file to restore your installation token and any other customized settings.
Tip: If you have multiple connectors installed for high availability, we recommend upgrading the standby connectors first, then promoting an upgraded standby connector to Active before upgrading the previously Active connector.
Note: CRL and OSCP certificate validations were added in LDC version 2.3.22. If upgrading from a prior version, ensure that your firewall allows outbound connections from your LDCs to *.digicert.com on port 80.
If you are upgrading your connector due to the TLS 1.0/1.1 deprecation and cannot make the necessary changes to your firewall by the deprecation deadline, you may instead install LDC version 2.3.21 (ZIP) (TGZ) to prevent user disruptions. Please update your firewall and your connectors at the soonest opportunity.
Monitoring an LDAP Directory Connector
The LDAP Directory Connector version 2.0 and above uses the Simple Logging Facade for Java (SLF4j). This framework uses an XML-formatted configuration file that you can edit to do the following:
- Set the directory path and filename to the connector log file
- Set the format of logged messages
- Set the threshold (
DEBUG, INFO, WARN, ERROR) of logged messages
- Set the log file rollover triggering policy (size, date, etc.)
- Set the log file rollover naming policy
- Set the maximum number of rolled over log files to keep
The LDAP Directory Connector is distributed with a default logging configuration file (embedded within the onelogin-ldc.jar file) that displays INFO, ERROR, and WARN messages, but omits more detailed DEBUG-level messages. It uses the following message format:
[2016-10-11 16:32:23,246] [ldc-main] INFO - Starting: OneLogin LDAP Directory Connector
[2016-10-11 16:32:23,246] [ldc-main] INFO - Version: 2.3.8
[2016-10-11 16:32:23,246] [ldc-main] INFO - Release Date: September 17, 2016 7:01:00 PM
[2016-10-11 16:32:23,247] [ldc-main] INFO - CONNECTOR: Started
The fields logged by default include:
- Date/time stamp
- Name of the java thread from which the log message was issued
- Message level (e.g.
INFO)
- Context-sensitive message
The LDAP Directory Connector distribution also includes an additional logging configuration file, ./conf/logback-debug.xml, which is preconfigured for DEBUG-level logging.
You can edit this config file as needed (or use it as a template to create your own) and reference it directly from the command line when you launch the LDAP Directory Connector, using the command-line option -Dlogback.configurationFile=./logback-debug.xml before the -jar command, like this:
$ java -Xms1g -Xmx2g -XX:+UseG1GC -XX:MaxGCPauseMillis=500 -Dlogback.configurationFile=./logback-debug.xml -jar onelogin-ldc.jar -f <config-file-path>
The default logging configuration rotates the file when it reaches 100MB. It looks like this:
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<appender name="commonlogfile" class="ch.qos.logback.core.rolling.RollingFileAppender">
<!--See also http://logback.qos.ch/manual/appenders.html#RollingFileAppender-->
<File>logs/ldap_connector.log</File>
<encoder>
<pattern>[%d{ISO8601}] |%t| %-5p - %m%n</pattern>
</encoder>
<filter class="ch.qos.logback.classic.filter.ThresholdFilter">
<level>INFO</level>
</filter>
<rollingPolicy class="ch.qos.logback.core.rolling.FixedWindowRollingPolicy">
<maxIndex>5</maxIndex>
<FileNamePattern>logs/ldc.%i.log.zip</FileNamePattern>
</rollingPolicy>
<triggeringPolicy class="ch.qos.logback.core.rolling.SizeBasedTriggeringPolicy">
<MaxFileSize>100MB</MaxFileSize>
</triggeringPolicy>
</appender>
<root level="DEBUG">
<appender-ref ref="commonlogfile" />
</root>
</configuration> |