| This article describes how to provision users from OneLogin to Slack using the Slack SCIM API.
Enable Provisioning
-
Go to Apps > Company Apps and select the Slack app to which you want to provision users.
-
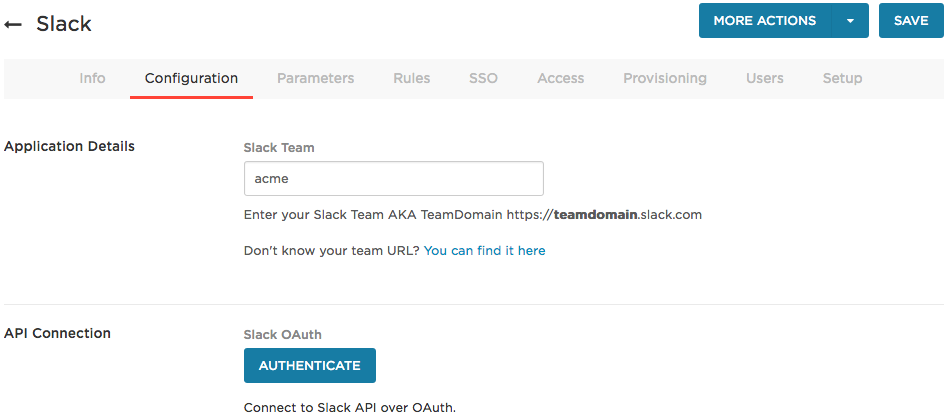
Go to the Configuration tab.
The Slack Team should already have been entered when you set up SSO for Slack.
-
Connect to the Slack SCIM API over OAuth.
Click Authenticate and follow the prompts to enter your Slack credentials over OAuth 2.0. These credentials require permissions to read and write to your Slack account using the Slack SCIM API.
Note: If you update the displayName field with the SCIM API and it returns an invalid_display_name error, deselect Allow members to change their display name in the Slack UI and repeat the operation. Note: for provisioning purposes, Slack usernames are limited to 21 characters and usernames longer than 21 characters will fail provisioning.
-
Go to the Provisioning tab.
-
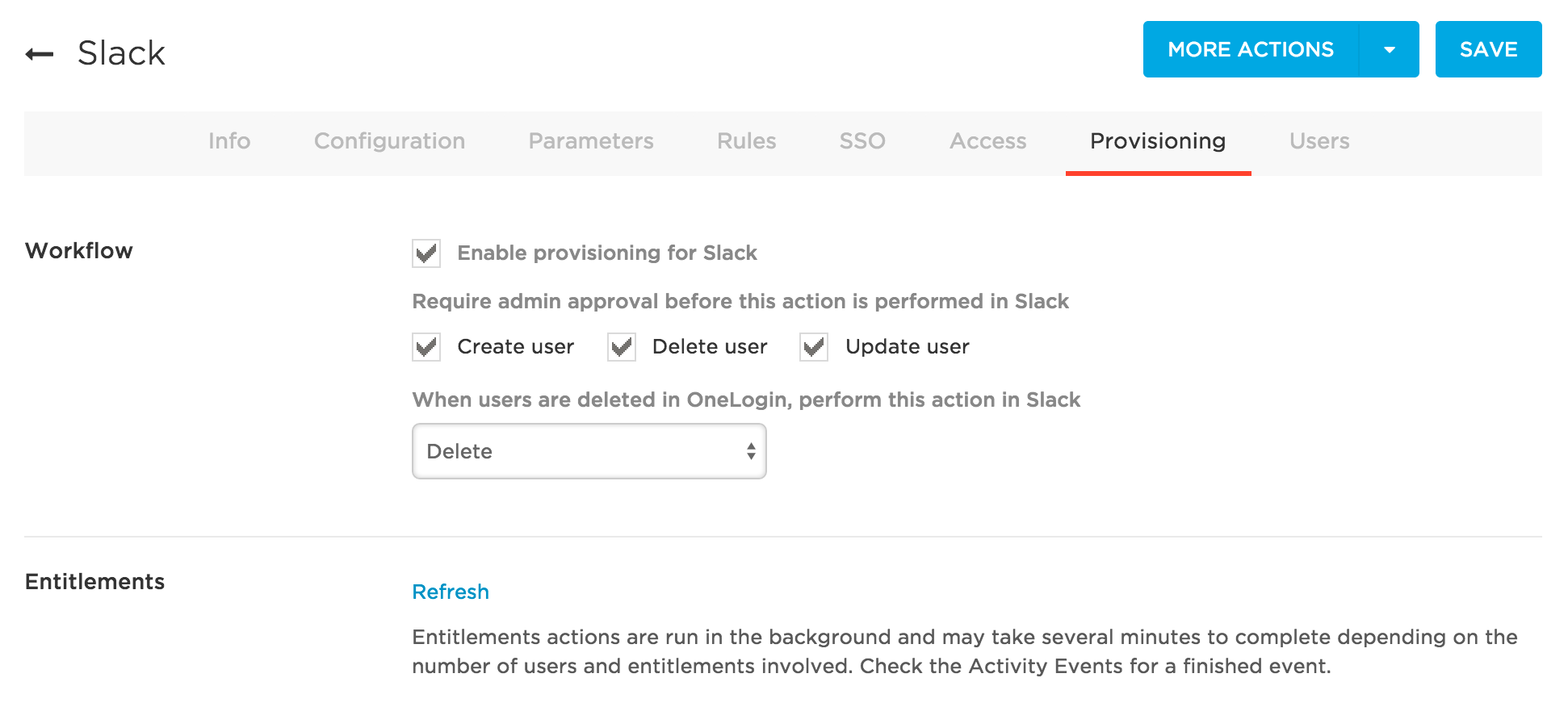
Select Enable provisioning for Slack. Once you enable this option and give users access to the app, the provisioning process will begin.
Note: You must select this option now to enable options required to complete subsequent steps. To ensure that you do not inadvertently provision users to Slack before you are ready, enable the action controls described in the next step.
-
Choose the provisioning actions for which you want to require administrator approval. For example, based on the settings in the screenshot above, any time a user is created, deleted, or updated, a OneLogin administrator will need to go to Users > Provisioning to manually approve or ignore each of these actions.
Enabling these action options is useful especially before you intend to start provisioning because with the Enable provisioning for Slack option selected, you may just trigger provisioning during the course of setup and testing. With this safeguard enabled, a OneLogin administrator can just choose to ignore any inadvertent provisionings.
Once you are done configuring and testing provisioning, you can update the settings to leave one or more action options clear if you want OneLogin to make the provisioning change in Slack without requiring administrative approval.
-
Select what happens to a user in Slack when that user is deleted from OneLogin.
Select Delete, Suspend, or Do Nothing.
- Click Save.
Map Slack Attributes to OneLogin Attributes
In this task, you'll map Slack user attributes to OneLogin user attributes. Attributes are split between required and optional; you can select which values you want to include or exclude. These mappings tell OneLogin how to populate user attribute values to Slack when provisioning users from OneLogin. If you have a OneLogin attribute value that you want to send over to populate a Slack field, you'll define it in this task.
Note: adding a custom user field parameter to the Slack app does not add that parameter to provisioning.
-
Go to Apps > Company Apps and select the Slack app to which you want to provision users.
-
Go to the Parameters tab.
-
Select Configured by admin.
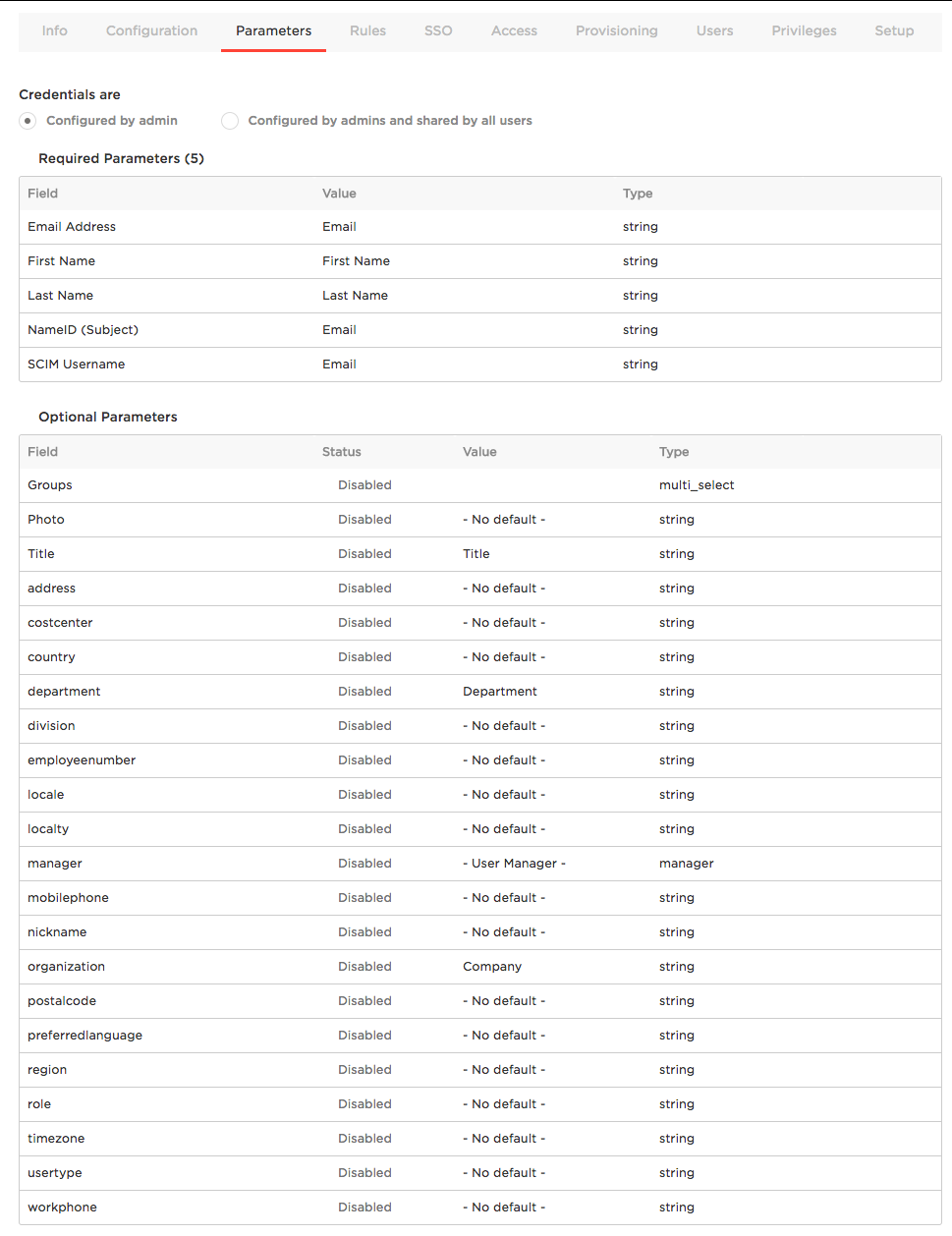
Use the Groups parameter to provision users to Slack user groups using the Slack SCIM API.
-
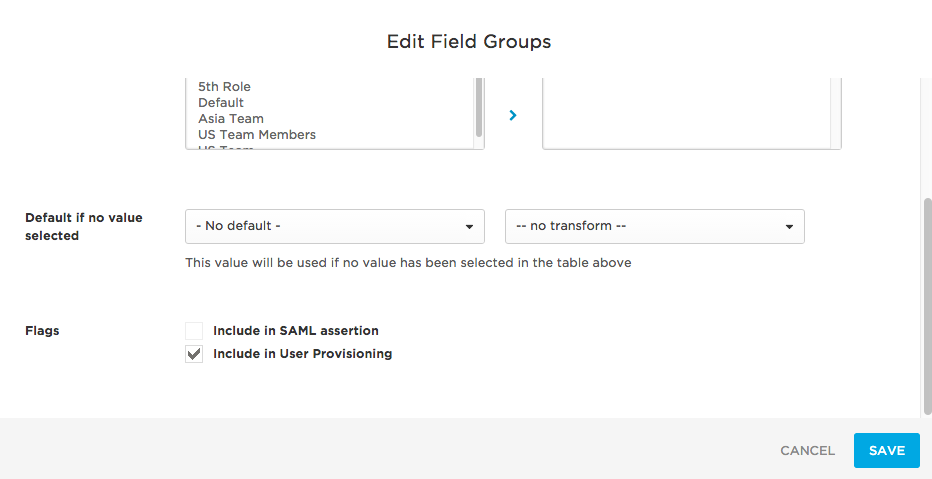
If you want to provision all of your users to one or more existing Slack user groups, configure provisioning using the Groups parameter alone. To do this, click the Groups parameter row and move the Slack user groups to which you want to provision users from the Available values column to the Selected values column. This configuration will provision all of your users to each of the selected Groups.
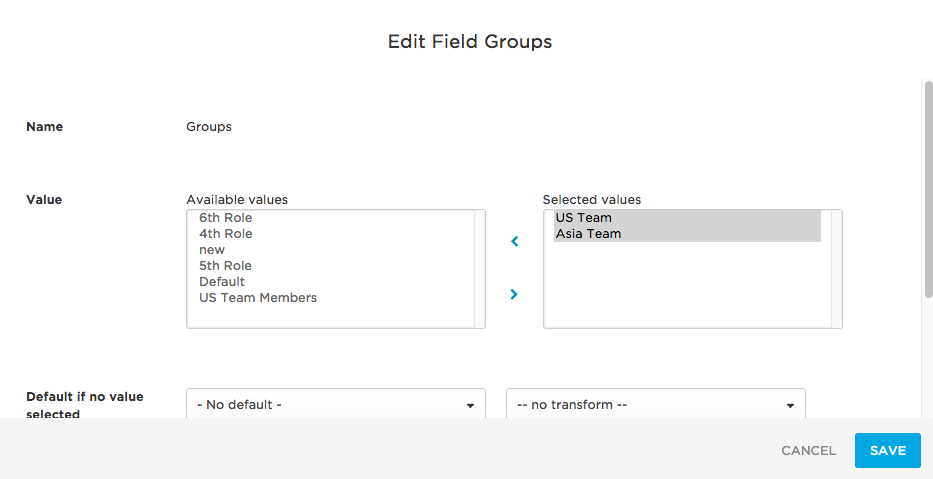
Note: To have your Slack user groups display as available values when configuring provisioning, you must first refresh entitlements. To do this, in your Slack app, go to the Provisioning tab and click Refresh.
Scroll down to select the Include in user provisioning option and click Save.
-
If you want to provision subsets of your users to one or more existing or new Slack user groups, configure provisioning using the Groups parameter and rules. See Using Rules to Provision Users to Slack User Groups.
-
If you do not want to provision to groups, be sure to leave the Include in User Provisioning option shown above clear.
-
The NameID (Subject) field is used for SAML SSO. See Configuring SAML SSO for Slack.
-
For SCIM Username, leave Value set to Email. While you can use a macro or another value here, Slack does an excellent job of parsing email values into usernames so we recommend that you set Value to Email.
-
Click Save.
Use Rules to Provision Users to Slack User Groups
You can define rules to provision subsets of your OneLogin users into Slack user groups. For example, you can define a subset of users by filtering on a specific OneLogin user attribute value and then define an action that provisions the subset of users to a specific Slack user group.
-
Go to Apps > Company Apps. Search for and select your Slack app.
-
Go to the Rules tab.
-
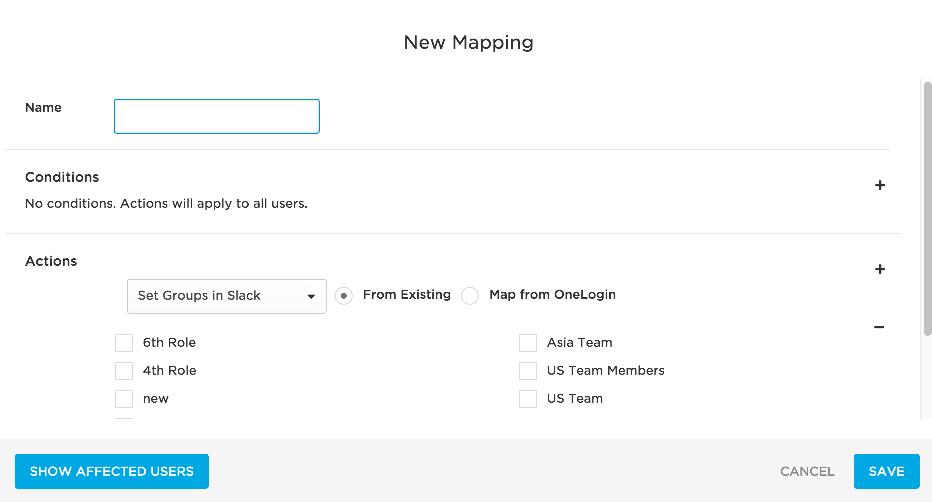
Click New rule to open the New Mapping dialog, where you can set the conditions and actions that determine which users will be provisioned from from OneLogin to specific Slack user groups.
-
Give your rule a name.
-
In the Conditions area, click + to add a condition. Use the fields to define a condition that defines a subset of users to be acted upon by the rule. Conditions are based on OneLogin user attribute values.
For examples, see Rule Mapping Examples below.
-
In the Actions area, click + to add an action. Use the fields to define the action that will be performed on users by the rule. Available actions include:
For examples, see Rule Mapping Examples below.
-
To see a list of users affected by the provisioning rule you've configured, click Show Affected Users. Review the list and refine your rule until only intended users are listed.
-
Once you are satisfied with your rule, click Save.
-
To add another provisioning rule, click New rule.
-
The order in which rules are applied matters and can impact provisioning results. Drag and drop the rule rows to put them in the order that produces correct results. To test results, see Testing Provisioning.
-
Click Save.
-
Go to the More Actions menu and click Reapply Provisioning Mappings to apply the new rule.
Important! You must reapply mappings any time you create or update rules!
Rule Mapping Examples
Here are some rule configuration examples that address common implementation scenarios.
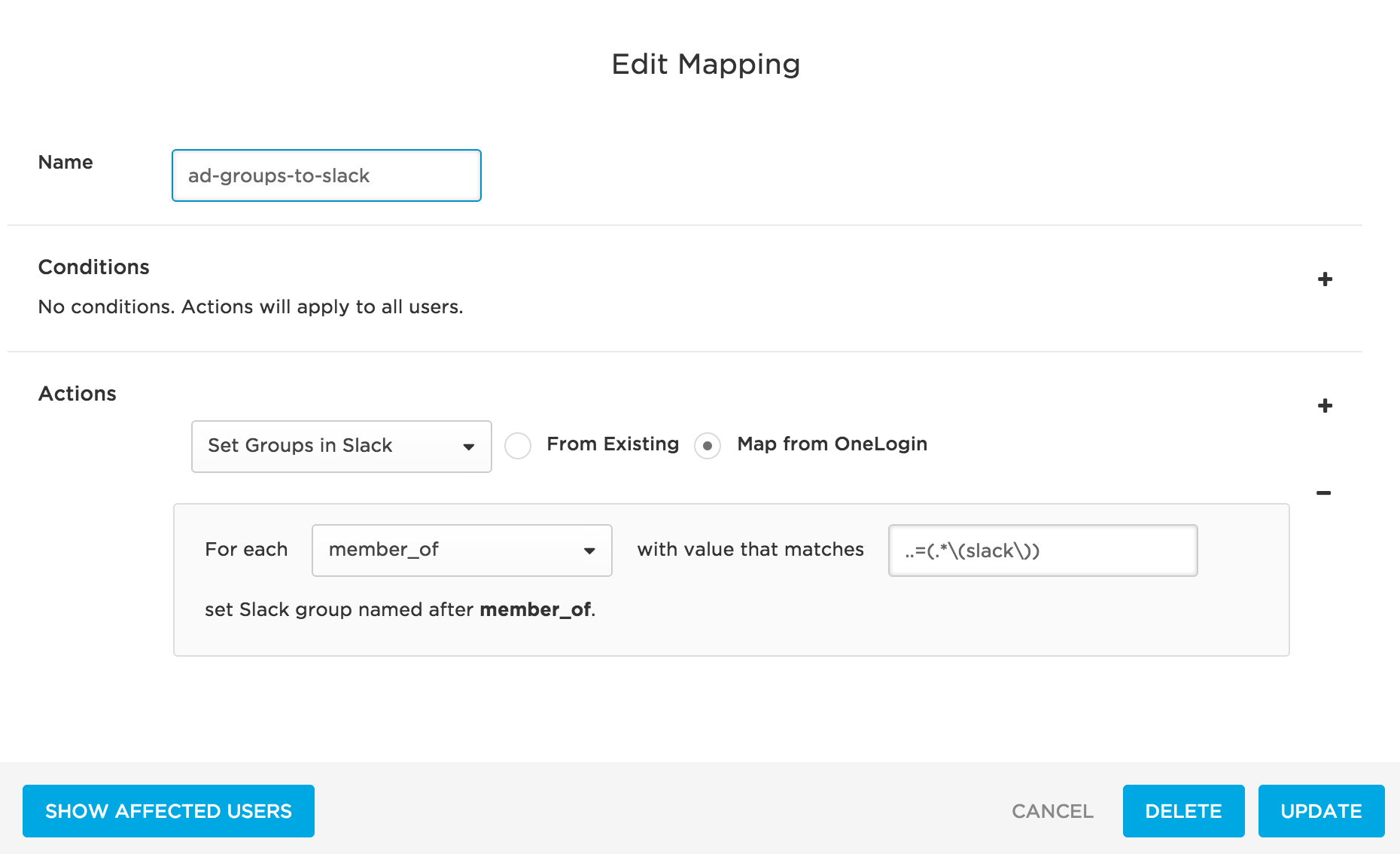
Provision Members of an AD/LDAP Security Group to New Slack User Groups
To do this, define a rule mapping like this one:
Conditions
For use cases like this one in which you are provisioning users to new Slack user groups, no conditions need to be set. All settings are configured in the Actions area.
Actions
-
In the first drop-down, select Set Groups in Slack App Name to provision OneLogin users to user groups in Slack.
-
Select the Map from OneLogin option to provision users to new Slack user groups created based on information in OneLogin.
-
Select a For each value of memberOf to provision users to Slack based on their member_of user attribute value.
The OneLogin member_of user attribute value is populated by Active Directory (AD) and reflects the user's membership in an AD/LDAP security group.
-
To identify the AD/LDAP security groups that will be used to create user groups in Slack and provision users to them, provide a regular expression (regex) in the adjacent field.
Provisioning will parse through AD/LDAP security group data and apply the regex. For each matching value, a user group will be created in Slack. Any users who are members of a matching AD/LDAP security group in OneLogin will be provisioned to the newly created user group in Slack.
For key regex guidance and examples, see Using Regex to Provision Members of AD/LDAP Groups to New App Groups.
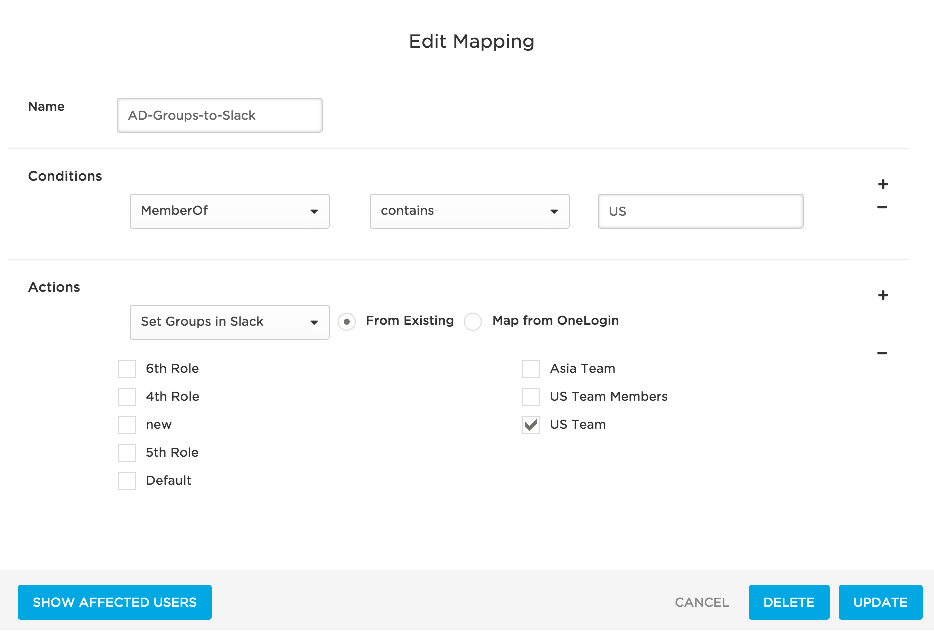
Provision Members of an AD/LDAP Security Group to an Existing Slack User Group
To do this, define a rule mapping like this one:
Conditions
-
In the first drop-down, select MemberOf to provision users based on their member_of user attribute value. The OneLogin member_of attribute value is populated by AD and reflects the user's membership in an AD/LDAP security group.
-
Use the two adjacent fields to write a condition to select the AD/LDAP security groups that contain the users that you want to provision to Slack.
Actions
-
In the first drop-down, select Set Groups in Slack App Name to provision users in the selected AD/LDAP security groups.
-
Select the From Existing option to provision users to an existing Slack user group.
-
Select the existing Slack user group to which you want to provision the users who are members of the selected AD/LDAP security group.
If you selected a subset of Slack user groups on the Parameters tab as discussed in Mapping Slack Attributes to OneLogin Attributes, only that subset of user groups will be selectable here.
Write Good Rules
Take the time to design your rules to produce provisioning results that are useful to your users. Be wary of writing rules that result in confusing or arbitrary provisioning. For example, take this rule that uses the regex J.*
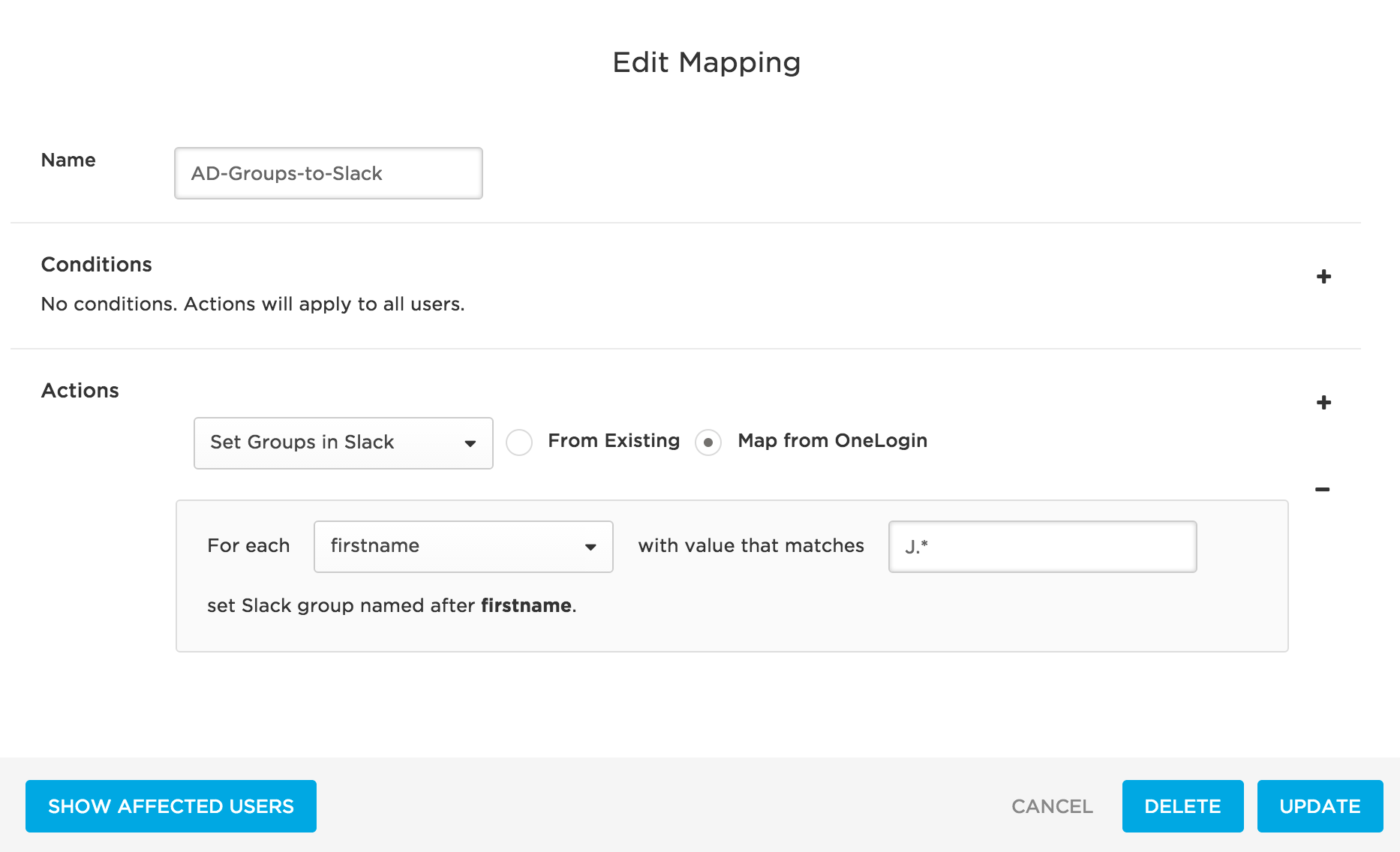
Consider provisioning applying the regex to each individual string in this comma-delimited list representing firstname user attribute values: Arturo, Benjamin, Cathy, Jennifer, John, Jonathan, Joshua, XiLin, Yelena, Zenith
This rule will take all firstname user attribute values that begin with J and create matching user groups in Slack and provision users to them. In this case, provisioning will create user groups in Slack for Jennifer, John, Jonathan, and Joshua. Users with the selected firstname values would then be provisioned to their matching user groups in Slack.
For most organizations, this rule would result in less-than-useful Slack user group creation and user provisioning.
Test Provisioning
Test your provisioning setup to confirm that provisioning from OneLogin to Slack is working.
-
Go to Apps > Company Apps. Search for and select your Slack app.
-
Go to the Provisioning tab. Ensure that the following options are selected for reasons described in Enabling Provisioning.

-
Click Save.
-
Go to Users > Roles.
-
Create a test role and add your Slack app to it.
-
Click Save.
-
Access the test role you just created.
-
Go to the Users tab.
-
Under Add Users to Role Manually, add your test user(s).
-
Click Save. This will trigger provisioning of the test user to your Slack app.
-
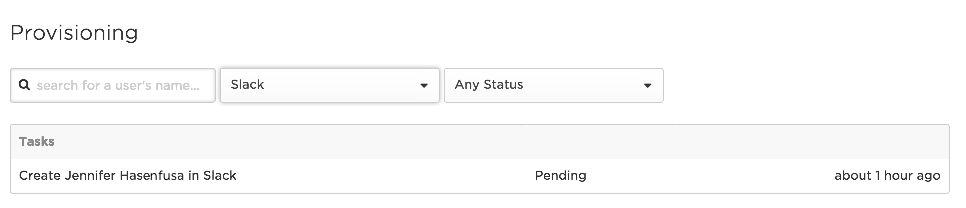
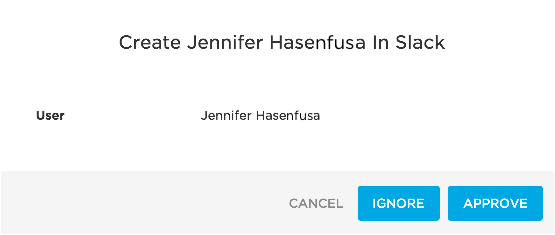
Per the settings in step 2, you must approve the provisioning action before it can proceed. To do this, go to Users > Provisioning. Use search and filters to locate your provisioning task. It should be in Pending status, as shown below:
-
Click the row. Click Ignore or Approve, depending on your test case.
-
If the provisioning row shows up as Failed on the Provisioning page, click the row to view a reason for the failure. Click Retry to try again.
-
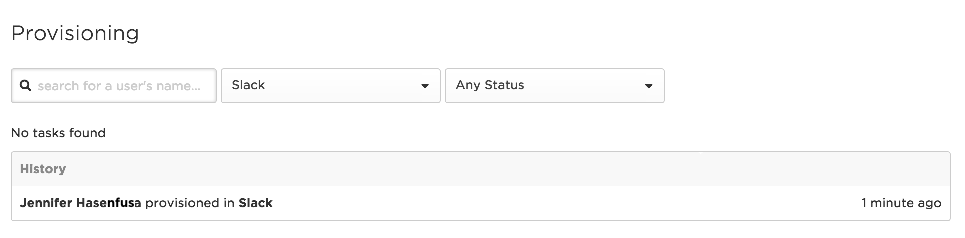
When the user has been successfully provisioned according to OneLogin, go to Slack and confirm that the new user has been added.
-
Continue to test for user updates and user deletions.
Upgrade Slack API authentication to OAuth
If you used the Slack SAML connector to add the SAML app to your OneLogin App Catalog before Sept 9, 2016, you were required to use a SCIM bearer token to authenticate to the Slack SCIM API. But now Slack lets you use OAuth 2.0 authentication without having to use a SCIM bearer token. Pure OAuth authentication is more secure, and you should switch your Slack API connection to use OAuth only.
- Log in to OneLogin as an admin.
- Go to Apps > Company Apps and select your Slack app.
-
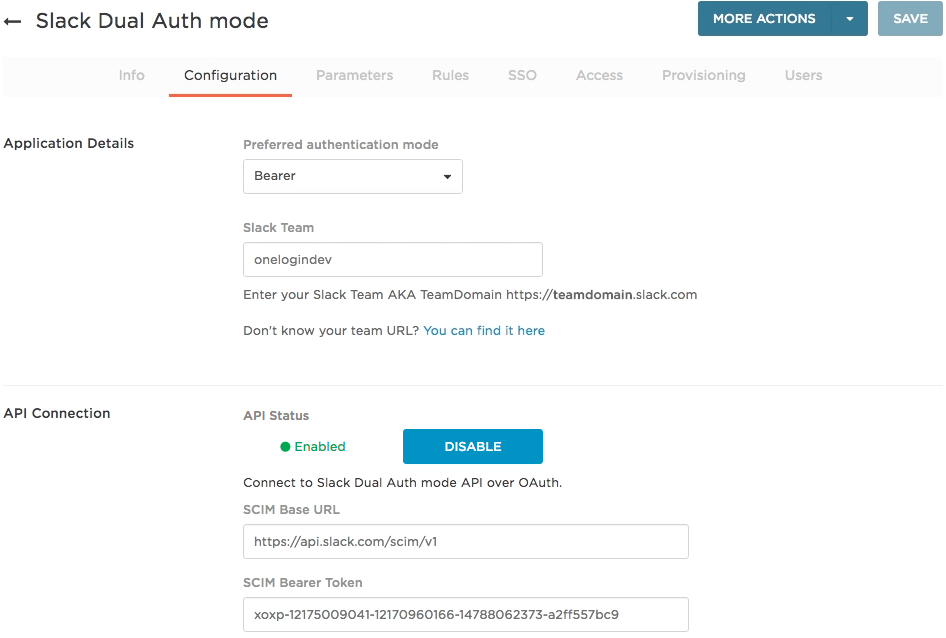
On the Configuration tab, click the Disable button to disconnect from the Slack SCIM API.
-
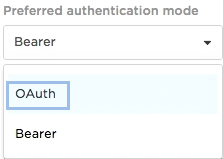
Select OAuth from the Preferred authentication mode drop-down.
- Click Save.
- Go back to the Configuration tab and click the Slack OAuth Authenticate button.
-
Click the link on the Complete Authentication Process dialog that pops up, and follow the prompts to authenticate to the Slack SCIM API over OAuth 2.0.
Your Slack credentials should have permissions to read and write to your company Slack account using the Slack SCIM API.
When the connection to the Slack SCIM API is complete, the Authenticate button will turn into a Clear Token button. You can click this any time you want to reauthenticate to the API.
|