If you manually added users to OneLogin or imported them into OneLogin from another source, such as Workday, you can provision those users to your LDAP directory.
Provisioning requires LDAP Directory Connector version 2 or above.
This article includes the following topics:
Prerequisites
Configure connectors to provision users from OneLogin to LDAP
-
In OneLogin, go to Users > Directories and select your LDAP directory.
-
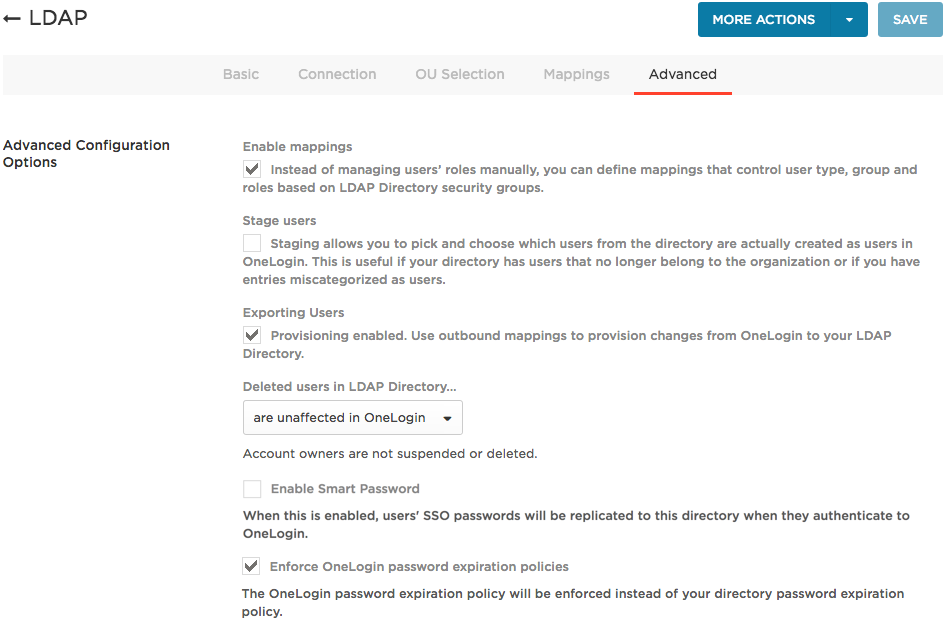
Go to the Advanced tab to enable user export from OneLogin to your LDAP directory.
-
Select Enable mappings to allow you to map LDAP directory attributes to OneLogin attributes to control user access to apps automatically. For more information, see Mappings. These mappings should not be confused with the mappings defined on the Mappings tab in the LDAP Directory Connector configuration pages.
-
Select Exporting users to enable OneLogin to provision users and user attribute updates to your LDAP directory.
-
Set Deleted users in LDAP Directory... to are unaffected in OneLogin since you are not provisioning users from your LDAP directory to OneLogin.
If you want the connector to delete users from the LDAP directory when they are deleted from OneLogin, you must:
- Turn Exporting users on
- Set all directory field mappings on the Mappings tab to be outbound (OneLogin to LDAP)
- Set the
ldc.ldap.delete property to true in the configuration file
See Install and Configure an LDAP Directory Connector 2 for more details about configuration properties.
-
Select Enable Smart Password to enable OneLogin to sync password changes from OneLogin to your LDAP directory.
Select to manage passwords in OneLogin (passing the SSO Password from OneLogin to LDAP). You can use Smart Password to synchronize users from another directory to this LDAP Directory: if your other directory syncs users to OneLogin and you enable Smart Password here, OneLogin captures your user's password from the other directory when they authenticate to OneLogin and syncs it to this LDAP Directory without forcing the user to do a password reset. If you use Smart Password for this migration or synchronization scenario, in which OneLogin merely functions as the middleman, the password isn't stored in OneLogin.
-
Click Save.
-
Go to the Mappings tab to switch the sync direction for the directory attributes you want to provision from OneLogin to your LDAP directory.
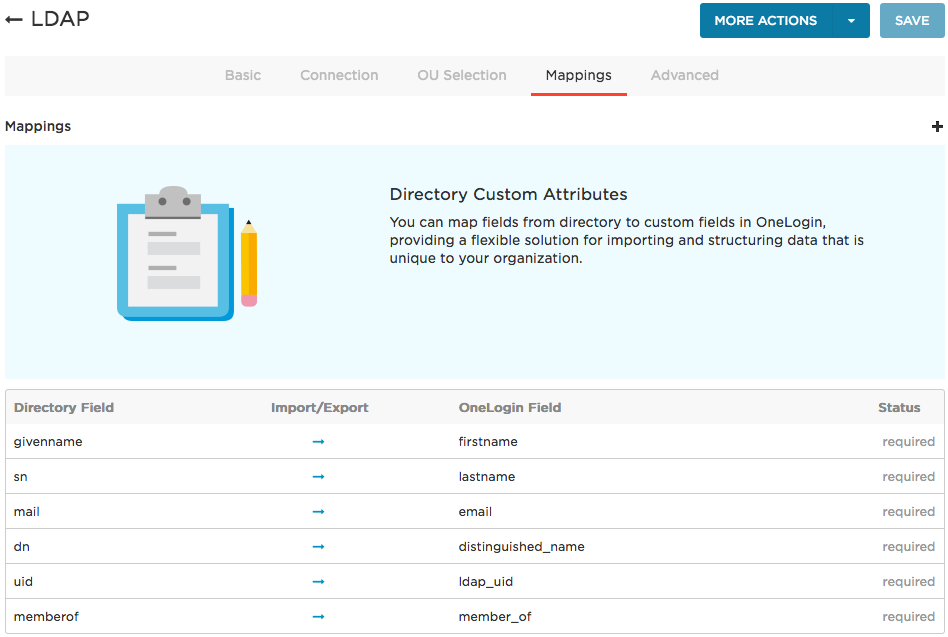
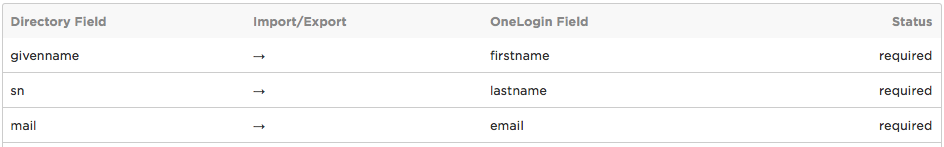
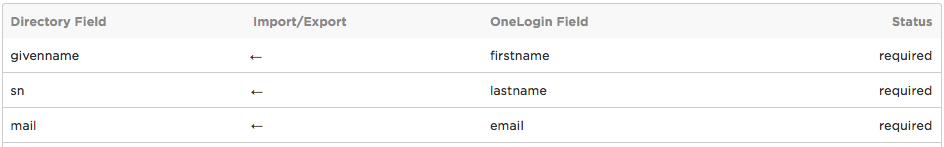
Click the arrow on the row for each attribute that you want to sync from OneLogin to your LDAP directory.
Before:
After:
-
(Optional) Add mappings to provision additional attributes from OneLogin to your LDAP directory.
To provision additional attributes from OneLogin to your LDAP directory, you must create custom user fields to hold the values that you want to pass to the LDAP directory attribute. See Custom User Fields.
-
On the Mappings tab, click the + (plus) button.
A new attribute row is added to the bottom of the list.
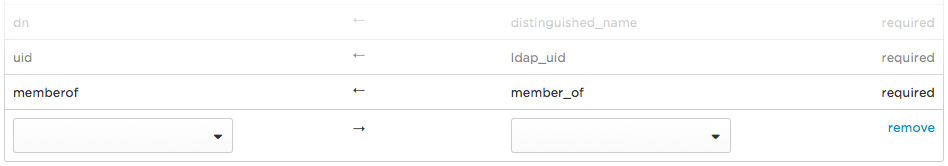
-
Select the LDAP Directory Field from the drop-down, and then select your custom field from the new OneLogin Field.
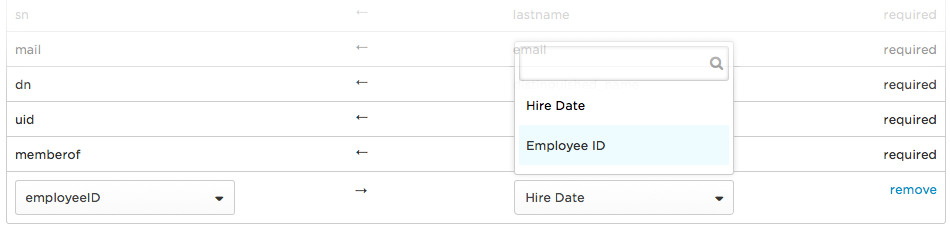
-
Click the arrow on the new attribute mapping row to switch the direction of sync to OneLogin -> LDAP directory.
-
Click Save.
-
Create rules (mappings) to trigger user attribute provisioning.
If you are provisioning new users from OneLogin to your LDAP directory, you must create rules that trigger provisioning and set the values that will populate the Distinguished Name and UID attributes in your LDAP directory.
You can also optionally use rules to establish how other attributes are provisioned to your LDAP directory. For example, you can write a rule that provisions all users in the Sales department to the Sales group in your LDAP directory.
For instructions and examples, see Creating rules to trigger provisioning and map OneLogin attributes, below.
Manager Export to LDAP
You can use custom attribute mappings to import and export the manager field between OneLogin and AD/LDAP.
To import the Manager field, set Manager by distinguished name.
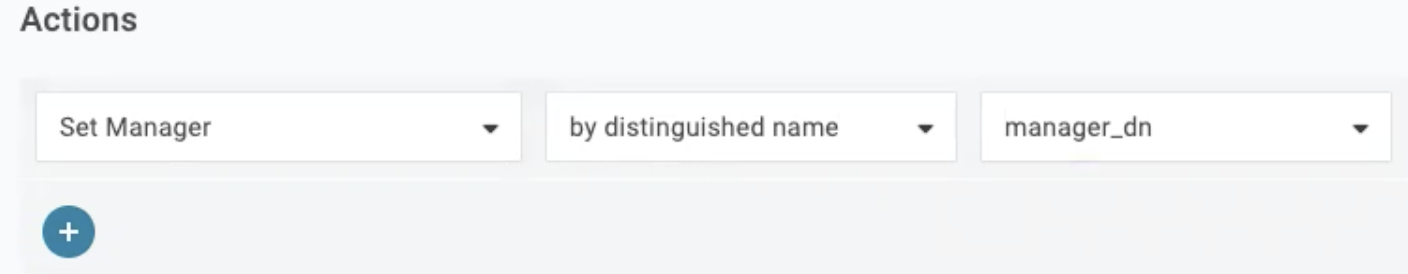
To export the Manager field, create a new mapping macro {manager_distinguished_name}.
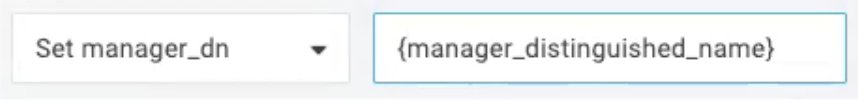
Create rules to trigger provisioning and map OneLogin attributes
You can write rules that trigger the provisioning of new OneLogin users to your LDAP directory and also determine how OneLogin attributes are provisioned to your LDAP directory. For example, you can write a rule that causes all users in the Sales department to be provisioned as memberOf the Sales group in your LDAP directory.
Note: These rules are also known as mappings, but should not be confused with the attribute mappings on the Mappings tab on the LDAP Directory Connector configuration page (as described in step 5, above).
Here are some guidelines for writing rules to support provisioning to your LDAP directory
-
Rules are optional unless you want to provision new users to your LDAP directory, in which case they are required.
In other words, if a user exists in OneLogin but not in your LDAP directory, typically that OneLogin user has no distinguished_name or ldap_uid value, and you must therefore create a rule that populates those two OneLogin user attributes.
-
It can also be helpful to create a rule that sets new OneLogin users to be authenticated by LDAP automatically.
All users whose Authenticated by value in the OneLogin user record is set to your LDAP directory are provisioned to your LDAP directory. Using a rule is easier than manually setting each user's Authenticated by value.
Such a rule is only required when there are OneLogin users that don't exist in your LDAP directory.
-
Mappings are also very handy for provisioning a user to particular LDAP attributes, such as groups (memberOf), based on OneLogin attributes.
Example 1: Set all new OneLogin users to be provisioned to your LDAP directory
In this example, we are provisioning all OneLogin users whose email includes your company email domain to the LDAP directory, setting their DistinguishedName and UID. Note that by mapping users with your company email domain, you are capturing all of your new users.
-
Go to Users > Mappings and click New Mapping.
-
Name the mapping and set the trigger Conditions and triggered Actions.
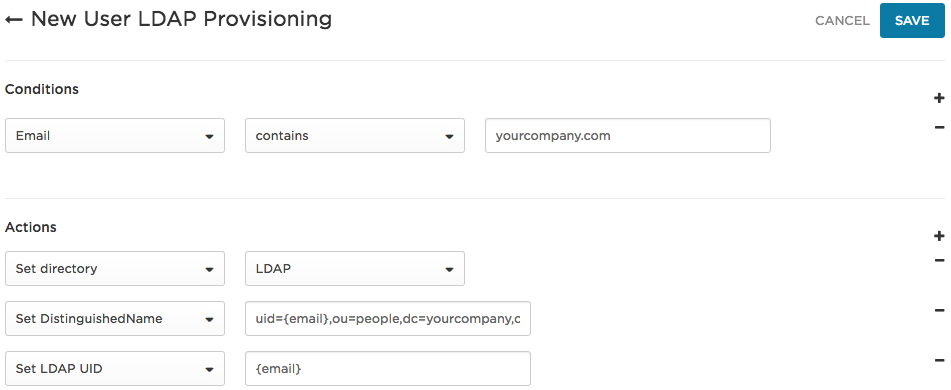
In this example, we set the Conditions to trigger a provisioning event whenever there is a new OneLogin user whose email domain includes yourcompany.
Under Actions:
- Set directory to LDAP means that all users that meet the conditions will be authenticated against the directory named "LDAP." This is essentially a way to do a bulk action to set the Authenticated by setting in the OneLogin user record.
-
Set DistinguishedName to uid={email},ou=people,dc=yourcompany,dc=com sets the user's DistinguishedName as it will be provisioned to the LDAP directory, with the uid set to the user's email address.
- Set LDAP UID to
{email} means that the OneLogin email value will be used as the UID in the LDAP directory.
-
Click Save.
-
On the Mappings page, click the Reapply All Mappings button to trigger provisioning.
Example 2: Set users in the Sales Department to be added to the Sales group in your LDAP directory
In this example, we are provisioning all OneLogin users in the Sales Department to the Sales group in your LDAP directory:
-
Go to Users > Mappings and click New Mapping.
-
Name the mapping and set the trigger Conditions and triggered Actions.
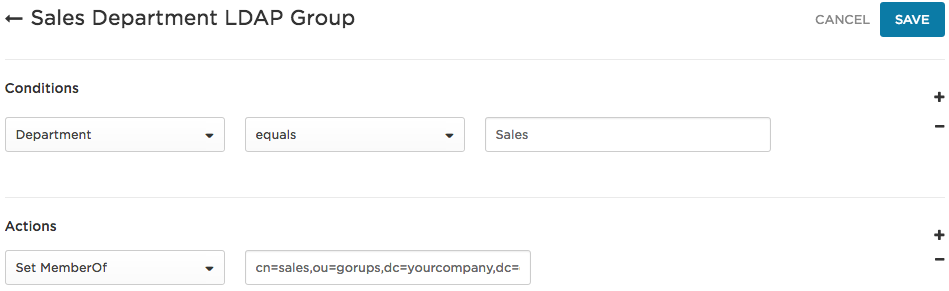
In this example, we set the Conditions to capture OneLogin users in the Sales Department.
We set the Actions to Set MemberOf to cn=sales,ou=groups,dc=yourcompany,dc=com, meaning that the users who meet the conditions will be provisioned to the sales group in the LDAP directory.
-
Click Save.
-
On the Mappings page, click the Reapply All Mappings button.
Note that you could combine the rules in Example 1 and Example 2 if you wanted to add users to your LDAP directory and set them to the Sales group in one mapping event. If you perform them separately, you must ensure that OneLogin runs the New User LDAP Provisioning rule (Example 1) before it runs the Sales Department LDAP Group rule (Example 2).
For more information, see Mappings. |