This article describes how to configure OneLogin to provide SSO for Atlassian Cloud apps using SAML.
******
In order to enable SAML single sign-on for Atlassian Cloud products you'll need to set up Atlassian Access, including a verified Atlassian Access domain. Learn more about Atlassian Access.
******
This connector works as a catch-all for all of your Atlassian Cloud apps, and works for both Service Provider (SP)-initiated SSO and Identity Provider (IdP)-initiated SSO from your OneLogin Portal.
If your organization uses more than one Atlassian Cloud app, clicking the app on your OneLogin Portal will take your users to the "default" Atlassian Cloud app, where they can click the application navigator ("hamburger") button to choose which Atlassian Cloud app they want.

Prerequisites
Your OneLogin users must be members of a verified domain in your Atlassian account. Only those users will be able to use SSO to log into Atlassian Cloud apps using SAML. You can verify domains by navigating to admin.atlassian.com. Note: You must be a Jira, Confluence, or Stride site admin to access this URL.
Configure SAML for Atlassian Cloud
-
Log into OneLogin as an admin.
-
Go to Apps > Add Apps, search for Atlassian Cloud, and select it.
-
On the initial Configuration tab, click Save to add the app to your Company Apps and display additional configuration tabs.
Tip. If you're setting up IdP-initiated SSO for a specific Atlassian Cloud app, such as JIRA or Confluence, you can change the Display name of the app here to reflect the app name that your users expect to see.
When you click Save, the Info tab appears.
-
Go to the Configuration tab and enter your Atlassian SAML ID
Optionally you may also add your Atlassian Site URL. This is required if you wish to launch the app from within OneLogin. If you don't enter a value here, your users will not be able to launch their Atlassian Cloud apps from the OneLogin portal.
If you want IdP-initiated SSO (launching apps from the OneLogin portal), you must enter the URL of your Atlassian Cloud account here. In other words, enter your JIRA Cloud or Confluence Cloud URL here. If you have multiple Atlassian Cloud apps, enter the URL for one of them here. Your users will be able to select other Atlassian Cloud apps from the Atlassian interface when they are logged in. See the introduction to this article, above, for an example.
Enter the entire URL, including protocol. For example, https://acme.atlassian.net.
-
Click Save.
-
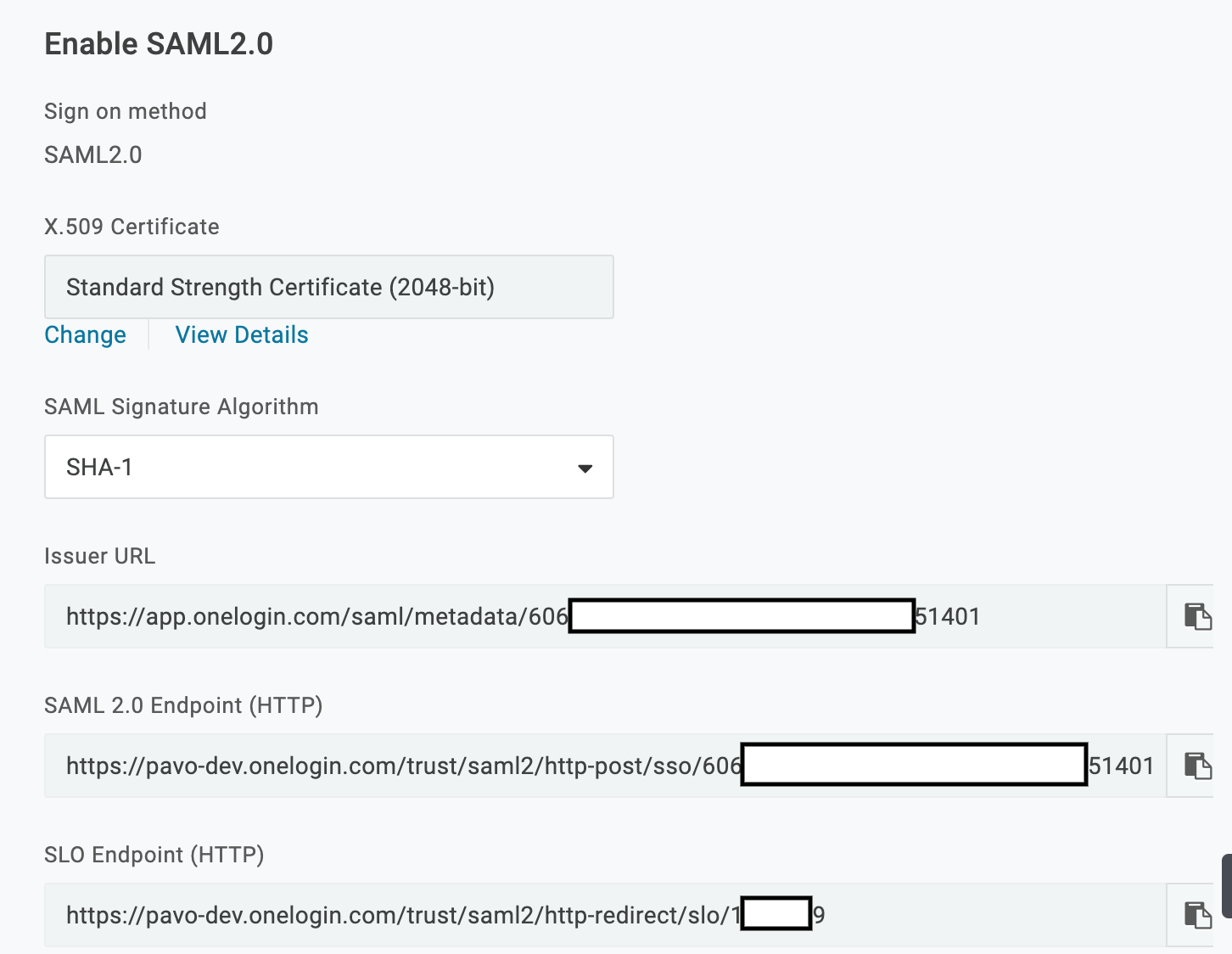
Go to the SSO tab to view the values that you'll copy to your Atlassian Cloud account in the steps that follow.
-
Open a new browser tab and log in to your Atlassian Cloud account as an admin at admin.atlassian.com.
-
Go to the SAML single sign-on page for your Atlassian Cloud account:
Go to admin.atlassian.com. Note: You must be a Jira, Confluence, or Stride site admin to access this URL. You can also go directly to the following URL:
-
Copy the following values from the SSO tab in OneLogin to the Atlassian Cloud SAML single sign-on page:
| Copy this OneLogin SSO field value: |
To this Atlassian Cloud field: |
| Issuer URL |
Identity provider Entity ID |
|
SAML 2.0 Endpoint (HTTP)
|
Identity provider SSO URL
|
|
X.509 Certificate
To get the X.509 Certificate, click View Details to open the certificate page. Copy the entire X.509 Certificate, including "----BEGIN CERTIFICATE----" and "----END CERTIFICATE----."
|
Public x509 Certificate
Paste the X.509 Certificate in its entirety into the x.509 field. Include "----BEGIN CERTIFICATE----" and "----END CERTIFICATE----."
|
-
Click Save configuration.
-
Return to OneLogin.
-
Go to the Parameters tab to verify the OneLogin attribute Values that will map to the Atlassian Cloud Fields in SAML requests.
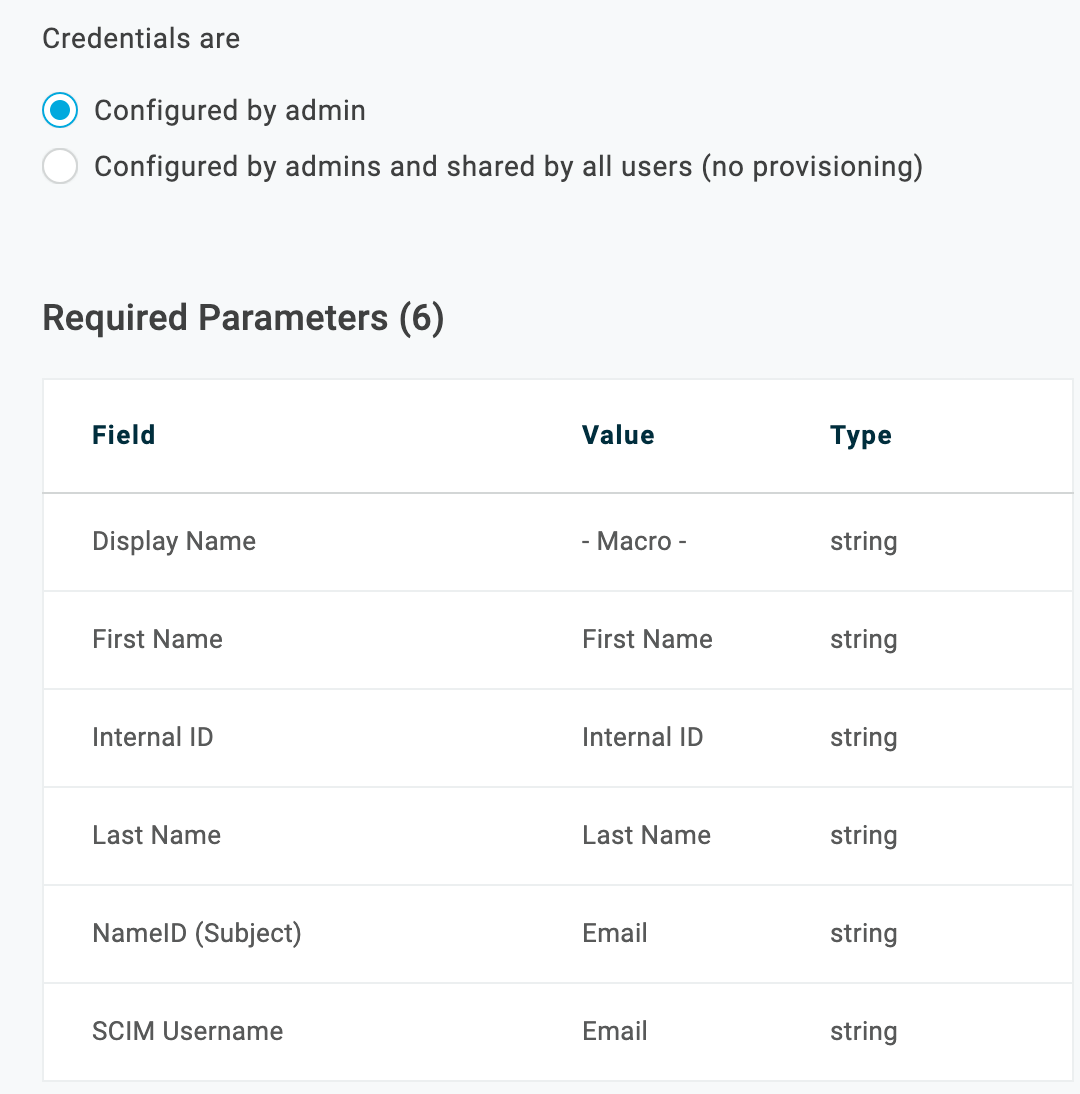
In most cases, you should keep the default mappings. If you need to change a mapping, click the parameter row to open the Edit Field Fieldname dialog, where you can select the OneLogin attribute Value you want to use.
In most cases, you should keep the Configured by admin default. For more information, see Setting Credential Configuration Options.
-
Go to the OneLogin Access tab to assign the OneLogin roles that should have access to Atlassian Cloud and provide any app security policy that you want to apply to Atlassian Cloud users.
You can also go to Users > All Users to add the app to individual user accounts.
Note. You may want to give access to yourself or a test account and test your completed OneLogin SAML integration with Atlassian Cloud before you assign additional roles on this tab. See step 16, below.
-
Click Save.
-
Test the SAML connection.
-
Ensure that you have a user account in both OneLogin and Atlassian Cloud that uses the same email.
You can create a test user, or you can use your own account if you choose.
-
Make sure that you are logged out of Atlassian Cloud.
-
Log in to OneLogin as an admin and give the test user (or yourself) access to the Atlassian Cloud app in OneLogin. (See step 14 above)
-
Log in to OneLogin as the test user.
-
Go to your Atlassian Cloud login page before your OneLogin session ends.
If the test user is granted access to Atlassian Cloud without having to provide login credentials, then SAML works.
You can find more information to help troubleshoot your Atlassian Cloud SAML integration in the Atlassian Cloud documentation.
See also: Provision Users to Atlassian Cloud. |